The Ultimate Guide to Threat Mitigation: Protecting Your Digital Assets from Cyber Attacks
Threat mitigation is the process of identifying, analyzing, and mitigating threats to an organization’s assets. It is a critical part of any organization’s security strategy, as it helps to protect against a wide range of threats, including cyberattacks, natural disasters, and insider threats.
There are many different ways to mitigate threats, and the best approach will vary depending on the specific threat. However, some common threat mitigation strategies include:
- Implementing security controls, such as firewalls, intrusion detection systems, and access control lists
- Developing and implementing security policies and procedures
- Educating employees about security risks
- Backing up data regularly
- Having a disaster recovery plan in place
Threat mitigation is an ongoing process, as new threats are constantly emerging. However, by taking a proactive approach to threat mitigation, organizations can protect themselves from a wide range of threats and minimize the impact of any security incidents that do occur.
Threat mitigation
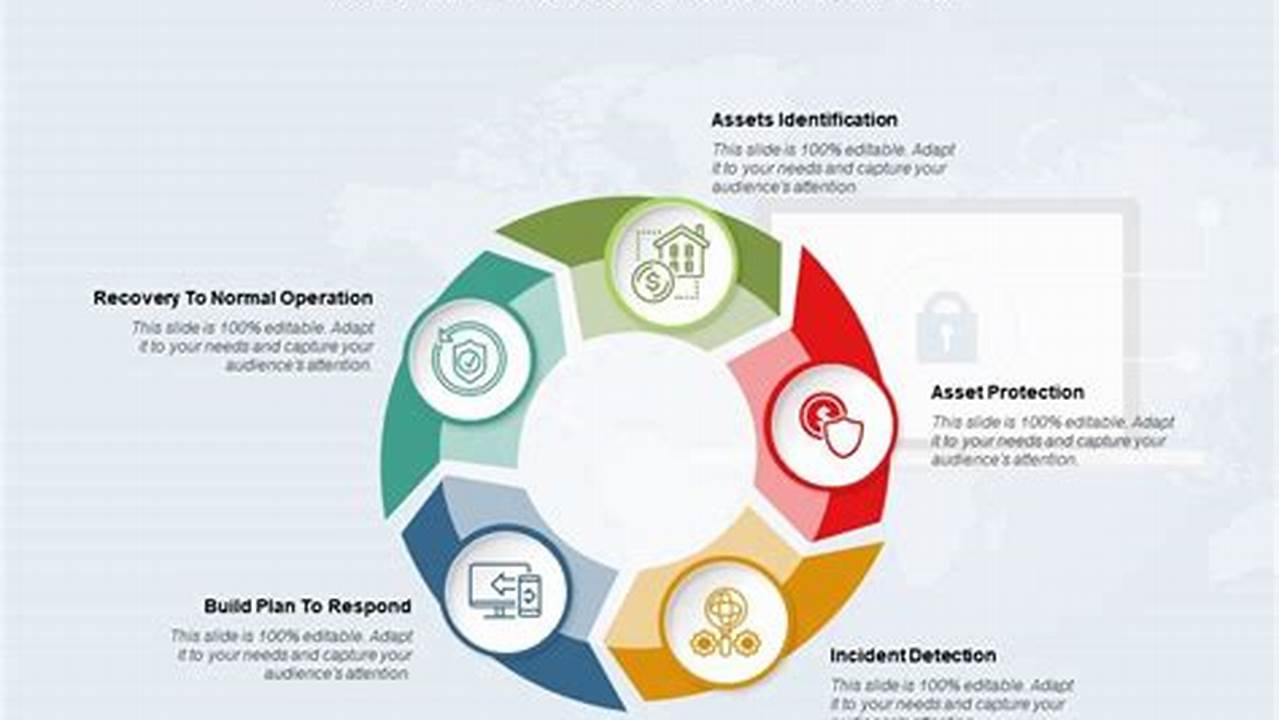
Threat mitigation is a critical aspect of any organization’s security strategy. It involves identifying, analyzing, and mitigating threats to an organization’s assets. There are many different ways to mitigate threats, and the best approach will vary depending on the specific threat. However, some common threat mitigation strategies include:
- Identification: Identifying threats is the first step to mitigating them. This can be done through a variety of methods, such as threat intelligence, vulnerability assessments, and security audits.
- Analysis: Once threats have been identified, they need to be analyzed to determine their likelihood and impact. This analysis will help to prioritize threats and allocate resources accordingly.
- Mitigation: Mitigation is the process of taking steps to reduce the likelihood or impact of threats. This can be done through a variety of methods, such as implementing security controls, developing security policies and procedures, and educating employees about security risks.
- Monitoring: Threat mitigation is an ongoing process, as new threats are constantly emerging. It is important to monitor the threat landscape and make adjustments to mitigation strategies as needed.
These are just a few of the key aspects of threat mitigation. By understanding these aspects, organizations can develop a more effective threat mitigation strategy and protect themselves from a wide range of threats.
Identification
Identifying threats is the first step to mitigating them because it allows organizations to understand the risks they face and take steps to protect themselves. Threat intelligence can provide organizations with information about the latest threats and vulnerabilities, while vulnerability assessments can help organizations identify weaknesses in their own systems. Security audits can also help organizations to identify security risks and ensure that they are taking appropriate steps to mitigate them.
For example, a company may use threat intelligence to learn about a new type of malware that is targeting businesses in their industry. The company can then use this information to update their security controls and protect themselves from the malware. Similarly, a company may use a vulnerability assessment to identify a weakness in their network security. The company can then patch the vulnerability and prevent attackers from exploiting it.
Identifying threats is an essential part of threat mitigation, and it is important for organizations to have a process in place for identifying and assessing threats. By understanding the threats they face, organizations can take steps to protect themselves and reduce the risk of a security incident.
Analysis
Analysis is a critical step in the threat mitigation process. It allows organizations to understand the risks posed by each threat and to prioritize their mitigation efforts. Without analysis, organizations would be unable to determine which threats are the most serious and which should be addressed first. This could lead to a waste of resources and could leave the organization vulnerable to attack.
For example, an organization may identify a number of threats to its network security, including malware, phishing attacks, and denial-of-service attacks. Through analysis, the organization can determine that malware is the most likely threat to occur and that it could have the greatest impact on the organization. The organization can then prioritize its mitigation efforts and focus on protecting against malware.
Analysis is an essential part of threat mitigation, and it is important for organizations to have a process in place for analyzing threats. By understanding the risks posed by each threat, organizations can prioritize their mitigation efforts and protect themselves from attack.
Mitigation
Mitigation is an essential part of threat mitigation as it allows organizations to take proactive steps to protect themselves from threats. By implementing security controls, developing security policies and procedures, and educating employees about security risks, organizations can significantly reduce the likelihood and impact of threats.
- Security Controls: Security controls are a set of measures that are implemented to protect an organization’s assets from threats. Security controls can include firewalls, intrusion detection systems, access control lists, and encryption. By implementing security controls, organizations can prevent unauthorized access to their assets and reduce the likelihood of a security breach.
- Security Policies and Procedures: Security policies and procedures are a set of rules and guidelines that define how employees should handle and protect sensitive information. Security policies and procedures can include policies on password management, data encryption, and incident response. By developing and implementing security policies and procedures, organizations can ensure that employees are following best practices for security and that there is a clear plan in place for responding to security incidents.
- Employee Education: Educating employees about security risks is an important part of threat mitigation. Employees are often the first line of defense against security threats, and by educating them about security risks and best practices, organizations can significantly reduce the likelihood of a security breach. Employee education can include training on topics such as phishing, malware, and social engineering.
Mitigation is an ongoing process, and organizations should regularly review and update their mitigation strategies to ensure that they are effective against the latest threats.
Monitoring
Monitoring is an essential component of threat mitigation. By monitoring the threat landscape, organizations can stay up-to-date on the latest threats and make adjustments to their mitigation strategies accordingly. This helps to ensure that organizations are always protected against the latest threats.
For example, an organization may use a threat intelligence service to monitor the threat landscape. The threat intelligence service will provide the organization with information about the latest threats and vulnerabilities. The organization can then use this information to update their security controls and protect themselves from the latest threats.
Similarly, an organization may use a vulnerability scanner to monitor their network for vulnerabilities. The vulnerability scanner will identify any vulnerabilities in the network and the organization can then patch the vulnerabilities and prevent attackers from exploiting them.
Monitoring is an essential part of threat mitigation and it is important for organizations to have a process in place for monitoring the threat landscape and making adjustments to their mitigation strategies as needed.
Threat Mitigation FAQs
Threat mitigation is an essential part of any organization’s security strategy. It involves identifying, analyzing, and mitigating threats to an organization’s assets. There are many different ways to mitigate threats, and the best approach will vary depending on the specific threat. However, some common threat mitigation strategies include implementing security controls, developing security policies and procedures, and educating employees about security risks.
Here are some frequently asked questions about threat mitigation:
Question 1: What is the most important aspect of threat mitigation?
Answer: The most important aspect of threat mitigation is identifying threats. This is because it allows organizations to understand the risks they face and take steps to protect themselves. Without identifying threats, organizations would be unable to mitigate them.
Question 2: How can organizations identify threats?
Answer: There are a number of ways to identify threats, including threat intelligence, vulnerability assessments, and security audits. Threat intelligence can provide organizations with information about the latest threats and vulnerabilities, while vulnerability assessments can help organizations identify weaknesses in their own systems. Security audits can also help organizations to identify security risks and ensure that they are taking appropriate steps to mitigate them.
Question 3: What are some common threat mitigation strategies?
Answer: Some common threat mitigation strategies include implementing security controls, developing security policies and procedures, and educating employees about security risks. Security controls are a set of measures that are implemented to protect an organization’s assets from threats. Security policies and procedures are a set of rules and guidelines that define how employees should handle and protect sensitive information. Employee education is also an important part of threat mitigation, as employees are often the first line of defense against security threats.
Question 4: How can organizations monitor threat mitigation effectiveness?
Answer: Organizations can monitor threat mitigation effectiveness by tracking security metrics, such as the number of security incidents and the average time to respond to security incidents. Organizations can also use threat intelligence to stay up-to-date on the latest threats and vulnerabilities.
Question 5: What are some best practices for threat mitigation?
Answer: Some best practices for threat mitigation include taking a proactive approach to threat mitigation, using a layered approach to security, and continuously monitoring the threat landscape. Organizations should also make sure to tailor their threat mitigation strategies to their specific needs and risks.
Question 6: What are the benefits of threat mitigation?
Answer: Threat mitigation can provide a number of benefits to organizations, including protecting their assets from damage or theft, reducing the risk of security breaches, and improving compliance with regulations. Threat mitigation can also help organizations to maintain their reputation and customer trust.
Summary: Threat mitigation is an essential part of any organization’s security strategy. By understanding the importance of threat mitigation and implementing effective threat mitigation strategies, organizations can protect their assets from a wide range of threats.
Transition to the next article section:
Threat Mitigation Tips
Threat mitigation is an essential part of any organization’s security strategy. By following these tips, organizations can protect their assets from a wide range of threats.
Tip 1: Identify threats
The first step to mitigating threats is to identify them. This can be done through a variety of methods, such as threat intelligence, vulnerability assessments, and security audits.
Tip 2: Analyze threats
Once threats have been identified, they need to be analyzed to determine their likelihood and impact. This analysis will help to prioritize threats and allocate resources accordingly.
Tip 3: Mitigate threats
Mitigation is the process of taking steps to reduce the likelihood or impact of threats. This can be done through a variety of methods, such as implementing security controls, developing security policies and procedures, and educating employees about security risks.
Tip 4: Monitor threats
Threat mitigation is an ongoing process, as new threats are constantly emerging. It is important to monitor the threat landscape and make adjustments to mitigation strategies as needed.
Tip 5: Use a layered approach to security
No single security measure is 100% effective. By using a layered approach to security, organizations can create a more robust defense against threats.
Tip 6: Educate employees about security risks
Employees are often the first line of defense against security threats. By educating employees about security risks and best practices, organizations can significantly reduce the likelihood of a security breach.
Tip 7: Tailor threat mitigation strategies to specific needs and risks
Not all organizations face the same threats. By tailoring threat mitigation strategies to specific needs and risks, organizations can ensure that their resources are being used effectively.
Tip 8: Continuously monitor the threat landscape
The threat landscape is constantly changing. By continuously monitoring the threat landscape, organizations can stay up-to-date on the latest threats and vulnerabilities.
Summary: By following these tips, organizations can develop a more effective threat mitigation strategy and protect their assets from a wide range of threats.
Transition to the article’s conclusion:
Threat Mitigation
Threat mitigation is a critical part of any organization’s security strategy. By identifying, analyzing, and mitigating threats, organizations can protect their assets from a wide range of risks. Threat mitigation is an ongoing process, and organizations should continuously monitor the threat landscape and adjust their mitigation strategies accordingly.
By taking a proactive approach to threat mitigation, organizations can reduce the likelihood and impact of security breaches. This will help to protect their reputation, customer trust, and bottom line.
Youtube Video:
