Behavioral threat detection is a specialized area of cybersecurity that focuses on identifying and mitigating threats based on behavioral analysis […]
Tag: threat
Cutting-Edge Endpoint Threat Prevention: Securing Endpoints
Endpoint threat prevention is a critical component of any cybersecurity strategy. It involves protecting endpoints, such as laptops, desktops, and […]
Master Real-time Threat Response Techniques for Unstoppable Cybersecurity
Real-time threat response is the practice of detecting, analyzing, and responding to security threats as they occur. It is a […]
Master Cybersecurity with Cutting-Edge Threat Monitoring
Cyber threat monitoring is the practice of continuously monitoring and analyzing networks, systems, and data for suspicious activity that could […]
Enhance Endpoint Security: Real-time Threat Detection and Protection
Endpoint threat detection is a crucial aspect of cybersecurity that involves identifying and responding to threats targeting endpoints, such as […]
Revolutionize Cybersecurity with Automated Threat Detection
Automated threat detection is the process of using software tools to identify and respond to potential threats in a timely […]
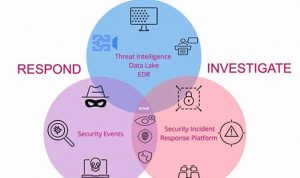
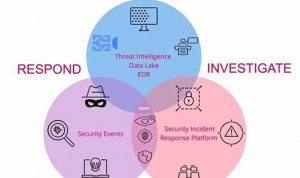
Comprehensive Guide to Threat Detection and Response: Protecting Your Digital Assets
Threat detection and response is the process of identifying and mitigating cybersecurity threats. It involves monitoring and analyzing network traffic, […]
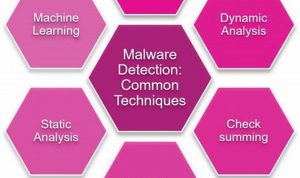
Ultimate Guide to Malware Threat Detection for Enhanced Cybersecurity
Malware threat detection is the process of identifying malicious software, such as viruses, worms, and trojan horses, before it can […]
Ultimate Guide to Security Threat Detection: Safeguard Your Cyber Stronghold
Security threat detection is the process of identifying and responding to potential threats to an organization’s security. These threats can […]
Unifying Threat Intelligence for Enhanced Cybersecurity
Threat intelligence integration is the process of collecting, analyzing, and sharing information about threats to an organization’s assets. This information […]