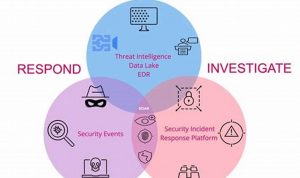
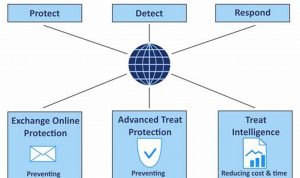
Endpoint threat monitoring is the practice of monitoring endpoints, such as laptops, desktops, and servers, for malicious activity. This can […]
Tag: threat
The Ultimate Guide to Threat Mitigation: Protecting Your Digital Assets from Cyber Attacks
Threat mitigation is the process of identifying, analyzing, and mitigating threats to an organization’s assets. It is a critical part […]
Essential Threat Response Tools for Robust Cybersecurity
Threat response tools empower organizations to proactively manage and mitigate potential risks and incidents. These tools provide real-time monitoring, threat […]
Automate Your Threat Response: Enhanced Security with Cutting-Edge Technology
Threat response automation is the use of technology to automate the detection, investigation, and response to cyber threats. This can […]
Unparalleled Threat Detection Platform | Enhanced Cyber Security
Threat detection platform is a software solution that helps organizations to identify, analyze, and respond to potential threats to their […]
Comprehensive Endpoint Threat Intelligence: Protect Your Devices
Endpoint threat intelligence gathers and analyzes data to provide comprehensive insights into potential threats and vulnerabilities at endpoints, which are […]
Uncover Hidden Threats: Advanced Threat Detection for Enhanced Cybersecurity
Threat detection technology refers to systems and tools that are designed to identify and respond to potential threats to an […]
Master the Art of Advanced Threat Protection: Your Cybersecurity Fortress
Advanced threat protection (ATP) is a comprehensive security solution that safeguards networks and systems from sophisticated and evolving cyber threats. […]
Strategies for Countering Cybersecurity Threats: A Comprehensive Guide
Cybersecurity threat response encompasses the processes and procedures employed to detect, analyze, and mitigate potential threats to an organization’s cybersecurity […]
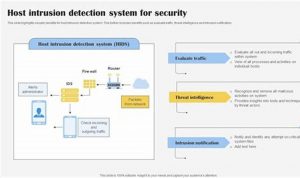
Protect Your Organization: Host Threat Detection for Enhanced Cybersecurity
Host threat detection is the process of identifying and responding to threats that target computer systems, networks, and applications. These […]