Security monitoring involves the continual oversight and analysis of security systems and logs to identify potential threats and suspicious activities. […]
Tag: security
Leading-Edge Endpoint Security: Comprehensive Protection Against Cyber Threats
Advanced endpoint security refers to comprehensive security measures designed to protect devices such as laptops, desktops, and mobile phones from […]
Security Operations: The Essential Guide to Securing Your Organization
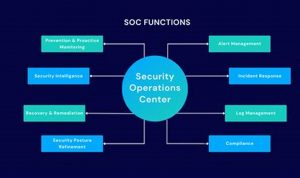
Security operations encompass the practices and processes employed to protect an organization’s assets from security breaches and cyberattacks. It involves […]
Master Endpoint Security Management for Bulletproof Cyber Defense
Endpoint security management is the practice of protecting endpoints, such as laptops, desktops, and mobile devices, from unauthorized access and […]
The Ultimate Guide to Mastering Security Event Management
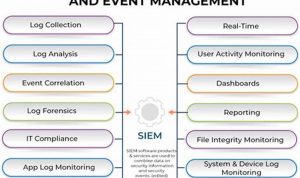
Security event management (SEM) is a process that involves collecting, monitoring, and analyzing security events to identify and mitigate potential […]