A security operations center (SOC) is a centralized facility that monitors and manages security events and incidents. SOCs are typically […]
Tag: security
The Ultimate Guide to Security Orchestration for Enhanced Cybersecurity
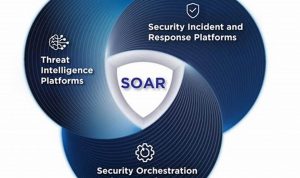
Security orchestration, a vital aspect of modern cybersecurity, enables organizations to automate and coordinate their security tools and processes, enhancing […]
Masterful Security Incident Management: Shielding Your Digital Fortress
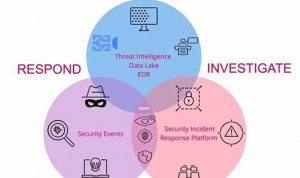
Security incident management is the process ofidentifying,responding to, and recovering from security incidents. It is a critical part of anyorganization’s […]
The Ultimate Guide to Security Event Correlation
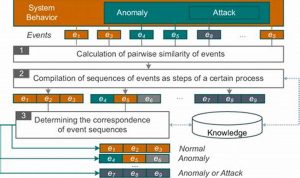
Security event correlation is the process of collecting and analyzing data from multiple security sources to identify and respond to […]
The Ultimate Guide to Automating Your Cybersecurity Defenses
Security automation refers to the use of software and tools to automate security tasks and processes, reducing the need for […]
Ultimate Guide: Security Risk Management for Enhanced Cyber Security
Security risk management is a crucial aspect of safeguarding sensitive information and critical assets against potential threats and vulnerabilities. It […]
Host-Based Security: The Ultimate Guide to Securing Your Servers
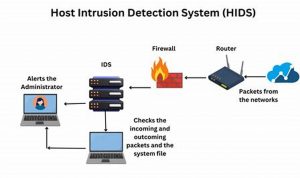
Host-based security refers to a comprehensive approach to protecting individual computer systems from unauthorized access, use, disclosure, disruption, modification, or […]
Ultimate Guide to Security Threat Detection: Safeguard Your Cyber Stronghold
Security threat detection is the process of identifying and responding to potential threats to an organization’s security. These threats can […]
Optimal Endpoint Security Platform: The Ultimate Defense for Your Cybersecurity
An endpoint security platform (ESP) is a software solution that protects endpoints, such as laptops, desktops, and mobile devices, from […]
Essential Endpoint Security Management: Protect Your Network from Cyber Threats
Security endpoint management refers to the security measures and technologies used to protect endpoints, which are devices such as laptops, […]