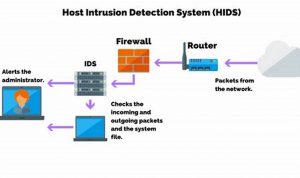
A host-based security system is a type of security system that is installed on a computer or other device. It […]
Tag: security
Early Warning System: Proactive Security Breach Detection for Enhanced Cybersecurity
Security breach detection is the process of identifying and responding to security breaches or attempted breaches. These can include unauthorized […]
Mastering Security Incident Handling: A Comprehensive Guide to Protect Your Cybersecurity
Security incident handling, a critical aspect of cybersecurity, involves the strategies and procedures implemented by organizations to detect, analyze, and […]
Master Security Information Management for Unstoppable Cyber Defense
Security information management (SIM) is the process of collecting, analyzing, and reporting on security-related information from multiple sources within an […]
Expert Endpoint Security Response for Enhanced Cyber Protection
Endpoint security response is a set of security measures designed to protect endpoints, which are devices such as laptops, desktops, […]
Comprehensive Security Intelligence for Robust Cybersecurity
Security intelligence refers to the process of gathering and analyzing data to identify, prevent, and respond to security threats. It […]
Complete Endpoint Security Guide for Enhanced Cyber Protection
Endpoint security is a critical component of any organization’s cybersecurity strategy. It involves protecting devices such as laptops, desktops, smartphones, […]
Network Security: The Ultimate Guide to Protecting Your Business
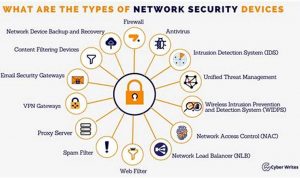
Network security is a broad term that encompasses the technologies and practices used to protect networks and data from unauthorized […]
The Ultimate Guide to Advanced Security Monitoring for Cybersecurity Pros
Advanced security monitoring is the practice of using advanced technologies and techniques to monitor security events and data in an […]
Ultimate Security Incident Response Guide for Bulletproof Cyber Defenses
Security incident response is the process of detecting, investigating, and responding to security incidents. It is a critical part of […]