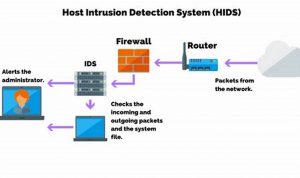
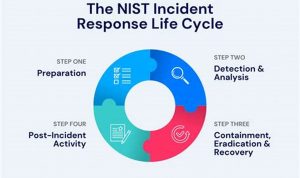
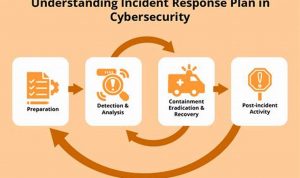
Cybersecurity incident response is the process of responding to and recovering from a cybersecurity incident. It involves identifying the incident, […]
Tag: incident
All-Encompassing Endpoint Incident Response Strategies
Endpoint incident response is a critical aspect of modern cybersecurity. It refers to the strategies and actions taken to detect, […]
Mastering Security Incident Handling: A Comprehensive Guide to Protect Your Cybersecurity
Security incident handling, a critical aspect of cybersecurity, involves the strategies and procedures implemented by organizations to detect, analyze, and […]
The Definitive Guide to Incident Detection and Response in Modern Cybersecurity
Incident detection and response is the process of identifying and responding to security incidents. It involves detecting suspicious activity, investigating […]
Ultimate Guide to Cyber Incident Response for Enhanced Cyber Security
Cyber incident response is the process of responding to and recovering from a cyber incident. It involves identifying the incident, […]
Ultimate Security Incident Response Guide for Bulletproof Cyber Defenses
Security incident response is the process of detecting, investigating, and responding to security incidents. It is a critical part of […]
Masterful Security Incident Management: Shielding Your Digital Fortress
Security incident management is the process ofidentifying,responding to, and recovering from security incidents. It is a critical part of anyorganization’s […]
Effective Incident Management: Strategies for Enhancing Security and Mitigating Risks
Incident management is a systematic approach to managing unplanned interruptions to an organization’s services or operations. An incident can be […]
Ultimate Guide to Cybersecurity Incident Handling for Optimal Cyber Resilience
Cybersecurity incident handling refers to the procedures and practices used to detect, analyze, contain, and recover from cyberattacks or data […]
Mastering Incident Response: A Guide to Mitigating Cyber Threats
An incident response plan is a set of procedures designed to help organizations respond to and recover from security incidents. […]