Host detection and response (HDR) is a crucial cybersecurity strategy that enables organizations to identify, contain, and remediate threats to […]
Tag: detection
Cyber Security's Guide to Advanced Detection and Response
Advanced detection and response is a security concept that involves using advanced technologies and techniques to detect and respond to […]
Ultimate Guide to Endpoint Breach Detection for Unstoppable Cybersecurity
Endpoint breach detection is a cybersecurity measure focused on identifying and responding to security breaches that target endpoints, the devices […]
Unparalleled Threat Detection Platform | Enhanced Cyber Security
Threat detection platform is a software solution that helps organizations to identify, analyze, and respond to potential threats to their […]
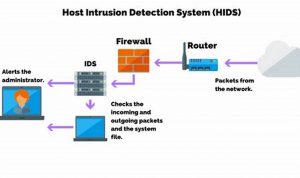
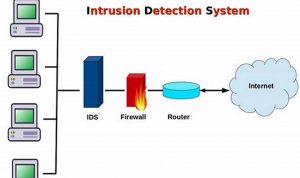
Secure Your Network with an Intrusion Detection System
An intrusion detection system (IDS) is a security mechanism used to detect unauthorized access to a computer system or network. […]
Early Warning System: Proactive Security Breach Detection for Enhanced Cybersecurity
Security breach detection is the process of identifying and responding to security breaches or attempted breaches. These can include unauthorized […]
Uncover Hidden Threats: Advanced Threat Detection for Enhanced Cybersecurity
Threat detection technology refers to systems and tools that are designed to identify and respond to potential threats to an […]
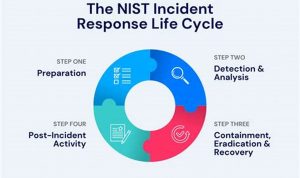
The Definitive Guide to Incident Detection and Response in Modern Cybersecurity
Incident detection and response is the process of identifying and responding to security incidents. It involves detecting suspicious activity, investigating […]
Uncover Hidden Breaches: Comprehensive Breach Detection Strategies
Breach detection is the process of identifying and responding to security breaches or attempted breaches. It involves monitoring network traffic, […]
Secure Your Endpoints: Comprehensive Endpoint Detection Platform for Cyber Threats
An endpoint detection platform (EPP) is a software solution that monitors and analyzes activities on endpoints (such as laptops, desktops, […]