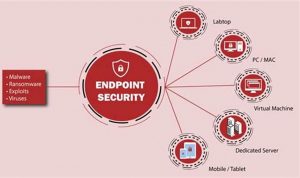
Endpoint attack prevention, a critical component of cybersecurity, involves safeguarding endpoints such as laptops, desktops, servers, and mobile devices from […]
Tag: attack
Cyber Security: The Ultimate Guide to Attack Detection Systems
An attack detection system (ADS) monitors a computer system or network for malicious activity or policy violations. It can detect […]
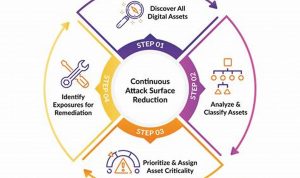
Ultimate Guide to Attack Surface Reduction: Enhancing Cybersecurity Posture
Attack surface reduction refers to the intentional reduction of the number of potential entry points that an attacker can use […]
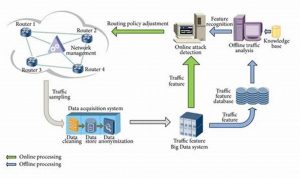
End-to-End Attack Detection for Enhanced Cyber Security
Attack detection is the process of identifying and responding to malicious activity on a computer system or network. It is […]
Instant Defense: Real-time Cyber Attack Detection and Mitigation
Real-time attack detection is a cybersecurity technique that monitors network traffic and activities for malicious or suspicious patterns in real […]