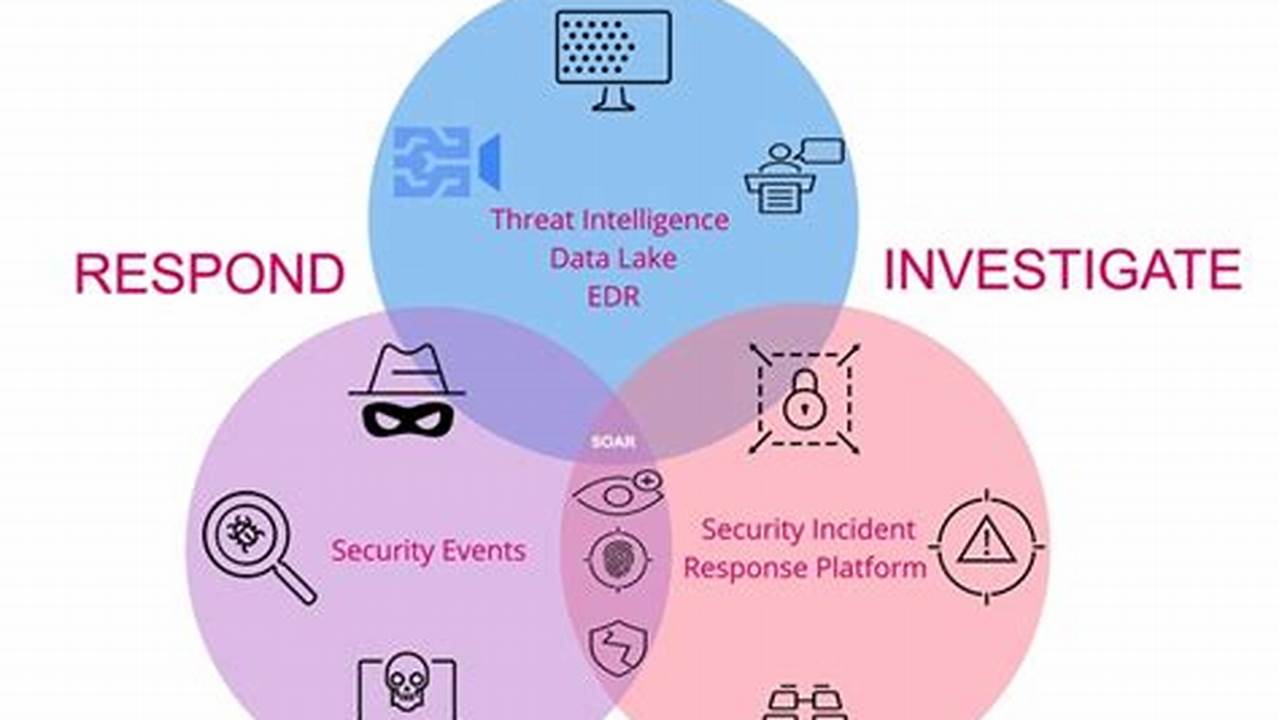
Security threat detection is the process of identifying and responding to potential threats to an organization’s security. These threats can come from a variety of sources, including malicious actors, natural disasters, and human error. Security threat detection is an important part of any organization’s security strategy, as it helps to identify potential threats and take steps to mitigate them before they can cause damage.
There are a variety of different security threat detection technologies and techniques that can be used to identify potential threats. These technologies and techniques can be used to monitor a variety of different data sources, including network traffic, system logs, and user activity. By monitoring these data sources, security analysts can identify potential threats and take steps to mitigate them.
Security threat detection is an important part of any organization’s security strategy. By identifying and responding to potential threats, organizations can help to protect their assets and their reputation.
Security threat detection
Security threat detection is a crucial aspect of cybersecurity, safeguarding organizations from potential risks and vulnerabilities. The following key aspects provide a comprehensive understanding of security threat detection:
- Identification: Recognizing and classifying potential threats to an organization’s security.
- Monitoring: Continuously observing and analyzing data sources to detect suspicious activities or patterns.
- Prevention: Implementing measures to proactively prevent threats from materializing or causing damage.
- Response: Developing and executing plans to effectively respond to and mitigate detected threats.
- Analysis: Examining threat data to understand their origins, patterns, and potential impact.
- Technology: Utilizing security tools and technologies to automate and enhance threat detection capabilities.
- Collaboration: Sharing threat intelligence and collaborating with external organizations to stay informed and address threats effectively.
These key aspects are interconnected and essential for a robust security threat detection system. By identifying threats early on, organizations can take prompt action to prevent or minimize their impact. Monitoring and analysis provide continuous visibility into potential threats, enabling organizations to adapt their security measures accordingly. Prevention and response strategies ensure that detected threats are effectively addressed, while technology and collaboration enhance the overall efficiency and effectiveness of the threat detection process.
Identification
Identification is the cornerstone of security threat detection. It involves recognizing and classifying potential threats to an organization’s security, enabling organizations to understand the nature and severity of threats they face.
- Threat intelligence gathering: Organizations collect and analyze threat intelligence from various sources to identify potential threats. This intelligence includes information about known vulnerabilities, emerging threats, and threat actor tactics, techniques, and procedures (TTPs).
- Vulnerability assessment and penetration testing: Organizations conduct vulnerability assessments and penetration tests to identify vulnerabilities in their systems and networks that could be exploited by attackers.
- Security monitoring: Organizations implement security monitoring tools and techniques to continuously monitor their systems and networks for suspicious activities that could indicate a potential threat.
- User awareness training: Organizations provide security awareness training to their employees to educate them about potential threats and how to recognize and report them.
Effective identification of potential threats is crucial for security threat detection. By understanding the different types of threats and their potential impact, organizations can prioritize their security measures and focus on mitigating the most critical threats.
Monitoring
Monitoring plays a crucial role in security threat detection, involving the continuous observation and analysis of data sources to identify suspicious activities or patterns that may indicate potential threats. Here are key facets of monitoring in relation to security threat detection:
- Data sources: Monitoring involves collecting and analyzing data from a variety of sources, including network traffic, server logs, application logs, user activity, and security events. This broad coverage enables organizations to detect threats across different layers of their IT infrastructure.
- Real-time analysis: Security monitoring tools leverage real-time analysis techniques to identify suspicious activities or patterns as they occur. This allows organizations to respond promptly to potential threats, preventing or mitigating their impact.
- Pattern detection: Monitoring systems employ pattern detection algorithms to identify anomalies or deviations from normal behavior. By recognizing unusual patterns, organizations can detect threats that may not be easily identifiable through traditional signature-based detection methods.
- Threat intelligence integration: Monitoring systems can be integrated with threat intelligence feeds to enhance threat detection capabilities. Threat intelligence provides information about known threats, vulnerabilities, and attack techniques, enabling organizations to stay informed about the latest threats and adjust their monitoring strategies accordingly.
Effective monitoring enables organizations to proactively detect potential threats, allowing them to take timely actions to mitigate risks and protect their systems and data.
Prevention
Prevention is a critical component of security threat detection, aiming to proactively prevent threats from materializing or causing damage to an organization’s systems and data. Its significance lies in mitigating risks before they escalate into full-blown incidents, ensuring the confidentiality, integrity, and availability of critical assets. Prevention measures play a vital role in reducing the impact of potential threats by actively addressing vulnerabilities and strengthening an organization’s security posture.
One key aspect of prevention is implementing strong access controls to restrict unauthorized access to sensitive data and systems. This includes enforcing password policies, implementing multi-factor authentication, and defining role-based access privileges. Additionally, organizations should regularly patch and update software and systems to address known vulnerabilities that could be exploited by attackers.
Another important preventive measure is deploying intrusion detection and prevention systems (IDS/IPS) to monitor network traffic and identify suspicious activities or patterns that may indicate an impending attack. IDS/IPS systems can be configured to detect and block malicious traffic, such as denial-of-service attacks or attempts to exploit known vulnerabilities.
Furthermore, organizations should implement security awareness training programs to educate employees about potential threats and how to recognize and report them. This training helps employees become an active part of the organization’s security defense by enabling them to identify and report suspicious emails, phishing attempts, or other potential threats.
By implementing robust prevention measures as part of their security threat detection strategy, organizations can significantly reduce the likelihood of successful attacks and minimize the impact of those that do occur. Prevention complements other security measures, such as detection, response, and analysis, to create a comprehensive security framework that safeguards an organization’s assets and reputation.
Response
Response is a crucial component of security threat detection, as it encompasses the development and execution of plans to effectively address and mitigate detected threats. It is the phase where organizations take decisive actions to contain, neutralize, and recover from security incidents.
When a security threat is detected, organizations must have a well-defined incident response plan in place to guide their actions. This plan should outline the roles and responsibilities of different teams, communication protocols, and procedures for containment, eradication, and recovery. A well-coordinated and timely response can significantly reduce the impact of a security incident and prevent it from escalating into a full-blown crisis.
Response measures may vary depending on the nature and severity of the detected threat. In the case of a malware infection, organizations may need to isolate infected systems, conduct forensic analysis, and implement remediation measures to remove the malware and prevent its spread. If a data breach has occurred, organizations may need to notify affected individuals, implement containment measures to prevent further data loss, and conduct a thorough investigation to determine the root cause and implement preventive measures.
Effective response to security threats requires a combination of technical expertise, clear communication, and collaboration across different teams within an organization. By having a robust response plan in place and regularly conducting incident response drills, organizations can enhance their ability to respond swiftly and effectively to security threats, minimizing potential damage and ensuring business continuity.
Analysis
Analysis is a critical component of security threat detection, involving the examination of threat data to understand their origins, patterns, and potential impact. By analyzing threat data, organizations can gain valuable insights that help them to prioritize their security measures and focus on mitigating the most critical threats.
Security threat detection systems generate a wealth of data that can be analyzed to identify trends, patterns, and potential threats. This data includes information about detected threats, such as their source, target, and method of attack. By analyzing this data, security analysts can identify common attack vectors, emerging threats, and the tactics, techniques, and procedures (TTPs) used by attackers.
Analysis also plays a crucial role in understanding the potential impact of threats. By assessing the severity and likelihood of potential threats, organizations can prioritize their security measures and focus on protecting their most critical assets. For example, an organization may decide to implement additional security controls to protect against a high-severity threat that is likely to occur, while a low-severity threat that is unlikely to occur may not require immediate attention.
In conclusion, analysis is a vital part of security threat detection, enabling organizations to understand the origins, patterns, and potential impact of threats. By analyzing threat data, organizations can gain valuable insights that help them to prioritize their security measures and focus on mitigating the most critical threats.
Technology
In the realm of security threat detection, technology plays a pivotal role in automating and enhancing the detection capabilities of organizations. By leveraging a wide range of security tools and technologies, organizations can streamline the detection process, improve accuracy, and respond more effectively to potential threats.
- Automation: Security tools can be automated to continuously monitor networks, systems, and applications for suspicious activities or patterns that may indicate a potential threat. This automation frees up security analysts from mundane and repetitive tasks, allowing them to focus on more strategic and complex aspects of threat detection.
- Enhanced detection capabilities: Security technologies, such as intrusion detection systems (IDS) and security information and event management (SIEM) systems, provide advanced threat detection capabilities. These technologies use sophisticated algorithms and machine learning techniques to identify and analyze large volumes of security data, detecting threats that may be missed by traditional methods.
- Improved threat intelligence: Security tools can be integrated with threat intelligence feeds, providing organizations with access to the latest threat information and attack techniques. This real-time intelligence allows organizations to stay informed about emerging threats and adjust their detection strategies accordingly.
- Centralized visibility and control: Security technologies provide a centralized platform for managing and monitoring security events across an organization’s IT infrastructure. This centralized visibility enables security analysts to quickly identify and respond to threats, reducing the risk of successful attacks.
The integration of technology into security threat detection has revolutionized the way organizations protect their assets and data. By automating detection tasks, enhancing detection capabilities, improving threat intelligence, and providing centralized visibility and control, technology has become an indispensable component of a robust security threat detection strategy.
Collaboration
Collaboration is an integral component of security threat detection, enabling organizations to stay informed about the latest threats and attack techniques, and to respond more effectively to potential threats. By sharing threat intelligence and collaborating with external organizations, organizations can gain access to a wider range of threat information, best practices, and resources, enhancing their overall security posture.
One important aspect of collaboration is the sharing of threat intelligence. Threat intelligence involves the collection and analysis of information about threats, including their origins, targets, methods of attack, and potential impact. By sharing threat intelligence with other organizations, organizations can gain a more comprehensive understanding of the threat landscape and identify emerging threats that they may not have been aware of on their own. This shared intelligence can help organizations to prioritize their security measures and focus on mitigating the most critical threats.
Another important aspect of collaboration is working with external organizations, such as law enforcement agencies, security vendors, and industry groups. By collaborating with external organizations, organizations can stay informed about the latest trends in cybercrime, emerging threats, and best practices for threat detection and response. This collaboration can also facilitate the sharing of resources and expertise, enabling organizations to better address complex security threats.
The benefits of collaboration for security threat detection are numerous. Collaboration can help organizations to:
- Gain access to a wider range of threat intelligence
- Identify emerging threats more quickly
- Prioritize their security measures more effectively
- Stay informed about the latest trends in cybercrime
- Share resources and expertise with other organizations
In conclusion, collaboration is an essential component of security threat detection. By sharing threat intelligence and collaborating with external organizations, organizations can stay informed about the latest threats and attack techniques, and respond more effectively to potential threats. This collaboration helps organizations to reduce their risk of successful attacks and protect their assets and data.
Frequently Asked Questions on Security Threat Detection
Security threat detection is a crucial aspect of cybersecurity, safeguarding organizations from potential risks and vulnerabilities. Frequently asked questions (FAQs) provide insights into common concerns and misconceptions surrounding security threat detection.
Question 1: What is the importance of security threat detection?
Security threat detection is essential for organizations to protect their assets and data from potential threats. It enables organizations to identify and respond to threats in a timely manner, preventing or mitigating their impact.
Question 2: What are the different types of security threats?
Security threats can vary widely, including malware, phishing attacks, ransomware, data breaches, and denial-of-service attacks. Organizations need to be aware of the diverse threat landscape and implement appropriate security measures.
Question 3: How can organizations improve their security threat detection capabilities?
Organizations can enhance their security threat detection capabilities by implementing a combination of measures, such as deploying security tools, monitoring network activity, conducting regular security audits, and providing security awareness training to employees.
Question 4: What is the role of collaboration in security threat detection?
Collaboration is vital in security threat detection, enabling organizations to share threat intelligence and best practices, stay informed about emerging threats, and coordinate incident responses.
Question 5: How can organizations measure the effectiveness of their security threat detection systems?
Organizations can measure the effectiveness of their security threat detection systems by evaluating metrics such as the number of detected threats, the accuracy of threat identification, the timeliness of response, and the overall reduction in security incidents.
Question 6: What are the future trends in security threat detection?
Future trends in security threat detection include the adoption of artificial intelligence (AI) and machine learning (ML) for automated threat detection, the integration of threat intelligence platforms, and the increasing emphasis on cloud-based security solutions.
These FAQs provide a comprehensive overview of the key aspects of security threat detection, empowering organizations to make informed decisions and strengthen their security posture.
For further information and expert guidance on security threat detection, refer to the main article sections below:
Security Threat Detection Best Practices
Implementing robust security threat detection measures is crucial for protecting organizations from potential risks and vulnerabilities. Here are some essential tips to enhance your security threat detection capabilities:
Tip 1: Deploy a Comprehensive Security Solution
Implement a multi-layered security solution that combines intrusion detection systems, firewalls, and endpoint protection software. This comprehensive approach provides a holistic defense against various types of security threats.
Tip 2: Monitor Network Activity Continuously
Establish continuous monitoring of network traffic to detect suspicious activities or anomalies. Utilize tools such as security information and event management (SIEM) systems to centralize and analyze security logs for potential threats.
Tip 3: Conduct Regular Security Audits
Perform regular security audits to identify vulnerabilities and configuration weaknesses in your systems and networks. Address identified issues promptly to reduce the risk of exploitation by attackers.
Tip 4: Provide Security Awareness Training
Educate employees about potential security threats and best practices. Empower them to recognize and report suspicious activities, reducing the likelihood of successful phishing attacks and other social engineering attempts.
Tip 5: Collaborate with External Security Experts
Partner with reputable security vendors and consult with cybersecurity experts to gain access to the latest threat intelligence and best practices. This collaboration enhances your organization’s ability to stay informed about emerging threats.
Tip 6: Leverage Artificial Intelligence and Machine Learning
Incorporate AI- and ML-powered security tools to automate threat detection and analysis. These technologies can significantly improve the accuracy and efficiency of threat identification.
Tip 7: Implement a Cloud-Based Security Strategy
Consider adopting cloud-based security solutions to enhance scalability, flexibility, and cost-effectiveness. Cloud providers offer a range of security services that can complement your existing security measures.
Tip 8: Measure and Improve Regularly
Establish metrics to measure the effectiveness of your security threat detection systems. Regularly review and analyze these metrics to identify areas for improvement and continuously enhance your security posture.
By implementing these best practices, organizations can significantly strengthen their security threat detection capabilities, proactively mitigate risks, and safeguard their valuable assets.
Conclusion
Security threat detection is a critical component of any organization’s cybersecurity strategy. By identifying and responding to potential threats, organizations can protect their assets, reputation, and business continuity.
This article has explored the key aspects of security threat detection, including identification, monitoring, prevention, response, analysis, technology, and collaboration. By understanding these aspects and implementing effective security threat detection measures, organizations can significantly reduce their risk of successful attacks and safeguard their valuable information and systems.
Youtube Video: