The Ultimate Guide to Security Orchestration for Enhanced Cybersecurity
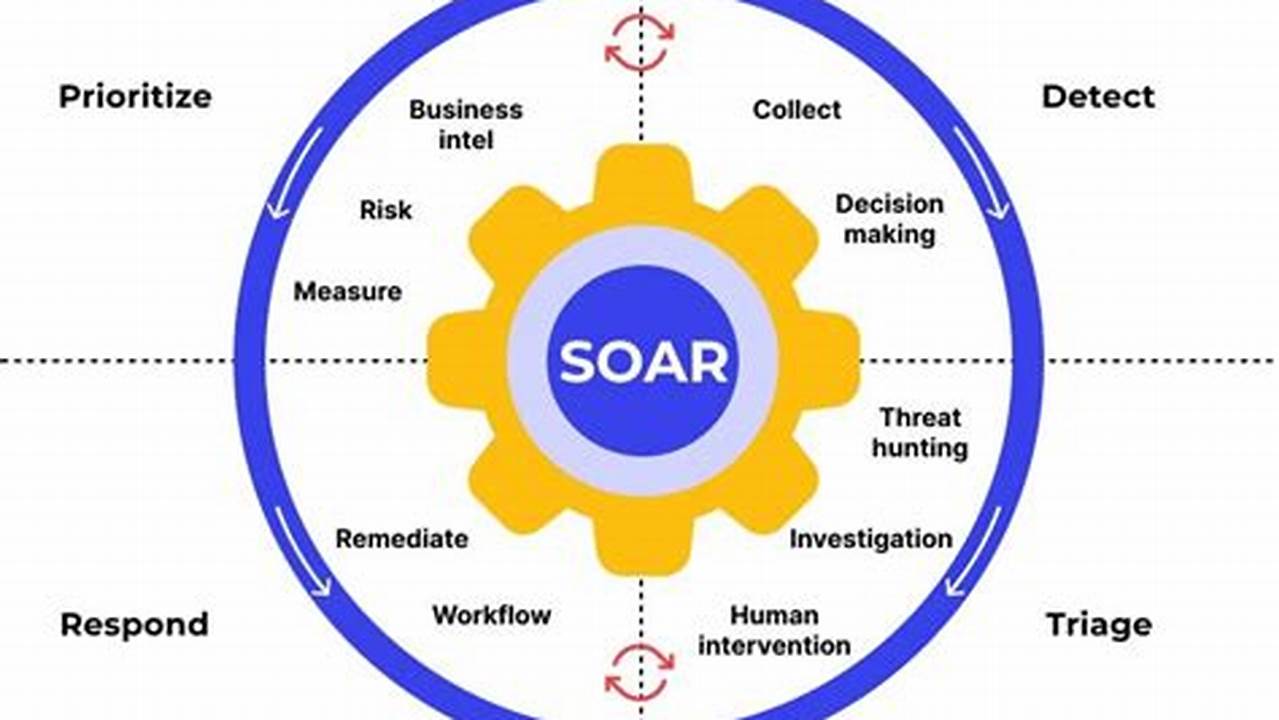
Security orchestration, a vital aspect of modern cybersecurity, enables organizations to automate and coordinate their security tools and processes, enhancing their overall security posture and response capabilities.
Security orchestration plays a crucial role in streamlining security operations, improving efficiency, and reducing the risk of security breaches. It empowers security teams to respond swiftly and effectively to security incidents by automating repetitive tasks, facilitating cross-functional collaboration, and providing real-time visibility into the security landscape.
The adoption of security orchestration has become increasingly important in today’s complex and evolving threat landscape. With the proliferation of sophisticated cyberattacks and the growing volume of security alerts, organizations need robust solutions that can help them orchestrate their security defenses and respond to threats in a timely and coordinated manner. Security orchestration is a key enabler in achieving this goal, offering numerous benefits including improved threat detection and response, enhanced security visibility, and reduced operational costs.
Security orchestration
Security orchestration, a critical component of modern cybersecurity, plays a vital role in enabling organizations to automate and coordinate their security tools and processes. It encompasses various key aspects that contribute to its effectiveness and importance:
- Automation: Automating repetitive tasks, expediting response times, and reducing manual errors.
- Coordination: Facilitating collaboration among security tools and teams, ensuring a unified response.
- Visibility: Providing a comprehensive view of the security landscape, enabling timely decision-making.
- Efficiency: Streamlining security operations, optimizing resource allocation, and reducing costs.
- Scalability: Supporting the management of complex and growing security environments.
- Flexibility: Adapting to evolving threats and security requirements, ensuring continuous protection.
- Integration: Seamlessly integrating with existing security tools and technologies, maximizing their value.
These key aspects collectively contribute to the effectiveness of security orchestration, enabling organizations to proactively address security challenges, minimize risks, and enhance their overall security posture. By automating tasks, coordinating responses, and providing comprehensive visibility, security orchestration empowers security teams to respond swiftly and effectively to threats, ensuring the protection of critical assets and data.
Automation
Automation is a fundamental component of security orchestration, enabling organizations to streamline their security operations and enhance their overall security posture. By automating repetitive and time-consuming tasks, security teams can significantly reduce the risk of human error and expedite response times to security incidents.
For instance, security orchestration can automate tasks such as security event monitoring, log analysis, and incident response. This allows security analysts to focus on more complex and strategic tasks, such as threat hunting and incident investigation. Additionally, automation can help organizations to enforce security policies and procedures consistently, ensuring that security measures are applied uniformly across the organization.
The benefits of automation in security orchestration extend beyond improved efficiency and reduced risk. Automation can also help organizations to improve their compliance with regulatory requirements and industry best practices. By automating security processes and workflows, organizations can ensure that they are meeting their compliance obligations and maintaining a high level of security.
Coordination
Coordination is a critical component of security orchestration, enabling organizations to break down silos between security tools and teams and facilitate a unified response to security incidents. Effective coordination ensures that all relevant security resources are working together seamlessly to detect, investigate, and respond to threats in a timely and efficient manner.
Security orchestration platforms provide a central hub for coordinating security tools and activities. They allow organizations to define workflows and playbooks that automate the communication and collaboration between different security tools and teams. This enables security teams to respond to incidents in a coordinated and consistent manner, reducing the risk of missed or delayed responses.
For example, in the event of a security breach, a security orchestration platform can automatically trigger an incident response workflow that notifies the appropriate security teams, collects relevant data from security tools, and initiates containment and remediation actions. This coordination ensures that all necessary steps are taken to contain the breach and minimize its impact.
Visibility
Visibility is a critical component of security orchestration, providing security teams with a comprehensive view of the security landscape and enabling them to make timely and informed decisions. Without visibility, security teams are operating in the dark, unable to identify potential threats or respond effectively to security incidents.
Security orchestration platforms aggregate data from multiple security tools and sources, providing a unified view of the security landscape. This allows security teams to correlate events, identify patterns, and detect threats that may not be apparent from any single source. For example, a security orchestration platform may combine data from intrusion detection systems, firewalls, and endpoint security tools to provide a complete picture of the organization’s security posture.
By providing visibility into the security landscape, security orchestration enables security teams to make more informed decisions about how to allocate resources, prioritize threats, and respond to incidents. This can help organizations to reduce their risk of security breaches and improve their overall security posture.
Efficiency
Efficiency is a critical component of security orchestration, enabling organizations to streamline their security operations, optimize resource allocation, and reduce costs. By automating repetitive tasks, coordinating security tools and teams, and providing visibility into the security landscape, security orchestration can significantly improve the efficiency of security operations.
For example, a security orchestration platform can automate the process of security event monitoring and response. This can free up security analysts to focus on more complex and strategic tasks, such as threat hunting and incident investigation. Additionally, security orchestration can help organizations to identify and prioritize security risks, enabling them to allocate resources more effectively.
The benefits of efficiency in security orchestration extend beyond cost savings. By streamlining security operations, organizations can improve their overall security posture. For example, by automating the process of security patching, organizations can reduce the risk of vulnerabilities being exploited by attackers.
Scalability
Scalability is a critical component of security orchestration, enabling organizations to manage the increasing complexity and volume of security data and events. As organizations adopt more cloud-based technologies and connect more devices to their networks, the amount of security data that needs to be collected, analyzed, and managed is growing exponentially.
- Elasticity: Security orchestration platforms can automatically scale up or down to meet the changing demands of the security environment. This ensures that organizations can always have the right amount of security resources available, without having to overprovision or underprovision.
- Centralized Management: Security orchestration platforms provide a centralized console for managing all security tools and data. This makes it easier for organizations to manage their security environment and respond to incidents in a timely manner.
- Integration with Third-Party Tools: Security orchestration platforms can integrate with a variety of third-party security tools. This allows organizations to leverage their existing investments in security technology and build a more comprehensive security solution.
- Automation: Security orchestration platforms can automate many of the tasks that are required to manage a security environment. This frees up security analysts to focus on more strategic tasks, such as threat hunting and incident investigation.
By providing these capabilities, security orchestration platforms help organizations to manage the complexity and volume of security data and events more effectively. This can lead to improved security posture, reduced risk of breaches, and lower costs.
Flexibility
Flexibility is a critical component of security orchestration, enabling organizations to adapt to the evolving threat landscape and changing security requirements. Security orchestration platforms provide the flexibility to integrate with a variety of security tools and technologies, allowing organizations to build a customized security solution that meets their specific needs.
For example, a security orchestration platform can be used to automate the process of security patching. This ensures that organizations can quickly and easily patch vulnerabilities, reducing the risk of exploitation by attackers. Additionally, security orchestration platforms can be used to automate the process of incident response. This helps organizations to respond to security incidents quickly and effectively, minimizing the impact of the incident.
The flexibility of security orchestration platforms is essential for organizations that want to maintain a strong security posture in the face of evolving threats. By providing the ability to integrate with a variety of security tools and technologies, and to automate security processes, security orchestration platforms help organizations to adapt to the changing threat landscape and ensure continuous protection.
Integration
Integration is a critical component of security orchestration, enabling organizations to maximize the value of their existing security investments and build a more comprehensive security solution. By integrating with a variety of security tools and technologies, security orchestration platforms can automate and streamline security processes, improve visibility into the security landscape, and enhance threat detection and response capabilities.
- Centralized Management: Security orchestration platforms provide a centralized console for managing all security tools and data. This makes it easier for organizations to manage their security environment and respond to incidents in a timely manner.
- Automated Workflows: Security orchestration platforms can automate many of the tasks that are required to manage a security environment. This frees up security analysts to focus on more strategic tasks, such as threat hunting and incident investigation.
- Improved Visibility: Security orchestration platforms can aggregate data from multiple security tools and provide a comprehensive view of the security landscape. This helps organizations to identify and prioritize security risks, and to make more informed decisions about how to allocate resources.
- Enhanced Threat Detection and Response: Security orchestration platforms can automate the process of threat detection and response. This helps organizations to quickly and effectively respond to security incidents, minimizing the impact of the incident.
By integrating with a variety of security tools and technologies, security orchestration platforms help organizations to maximize the value of their existing security investments and build a more comprehensive and effective security solution.
FAQs on Security Orchestration
This section provides answers to frequently asked questions about security orchestration. These questions address common concerns or misconceptions about security orchestration, providing a deeper understanding of its benefits and implementation.
Question 1: What is security orchestration?
Security orchestration is the process of automating and coordinating security tools and processes to improve efficiency, visibility, and response times. It enables organizations to manage their security operations more effectively and respond to security incidents more quickly and effectively.
Question 2: What are the benefits of security orchestration?
Security orchestration provides numerous benefits, including improved threat detection and response, enhanced security visibility, reduced operational costs, and improved compliance.
Question 3: How does security orchestration work?
Security orchestration platforms integrate with various security tools and technologies, enabling them to communicate and collaborate more effectively. They provide a centralized dashboard for managing security operations, automating workflows, and providing visibility into the security landscape.
Question 4: What are the challenges of implementing security orchestration?
Implementing security orchestration can be challenging due to the complexity of security environments, the need for skilled personnel, and the potential for integration issues. However, the benefits of security orchestration outweigh the challenges, making it a worthwhile investment for organizations.
Question 5: What are the best practices for implementing security orchestration?
Best practices for implementing security orchestration include starting with a clear understanding of the organization’s security needs, selecting the right platform, and integrating it with the organization’s existing security tools and technologies.
Question 6: What is the future of security orchestration?
Security orchestration is expected to continue to evolve, with increased adoption of artificial intelligence (AI) and machine learning (ML) to improve threat detection and response capabilities. Integration with cloud-based security services and the adoption of security orchestration as a managed service are also expected.
In summary, security orchestration is a critical component of modern cybersecurity, enabling organizations to improve their security posture, respond to threats more effectively, and reduce the risk of security breaches.
Proceed to the next section to learn more about the implementation and benefits of security orchestration.
Security Orchestration Tips
Security orchestration is a powerful tool that can help organizations to improve their security posture and respond to threats more effectively. Here are five tips for implementing and using security orchestration:
Tip 1: Start with a clear understanding of your organization’s security needs. This will help you to identify the right security orchestration platform and to configure it to meet your specific requirements.
Tip 2: Select the right security orchestration platform. There are a number of different security orchestration platforms available, so it is important to choose one that is a good fit for your organization’s size, budget, and security needs.
Tip 3: Integrate your security orchestration platform with your existing security tools and technologies. This will allow you to automate and coordinate your security operations more effectively.
Tip 4: Use security orchestration to automate repetitive tasks. This will free up your security analysts to focus on more strategic tasks, such as threat hunting and incident investigation.
Tip 5: Use security orchestration to improve your incident response capabilities. Security orchestration can help you to respond to security incidents more quickly and effectively, minimizing the impact of the incident.
By following these tips, you can implement and use security orchestration to improve your organization’s security posture and respond to threats more effectively.
Security orchestration is a critical component of a modern security program. By automating and coordinating your security tools and processes, you can improve your efficiency, visibility, and response times. This will help you to protect your organization from a wide range of threats.
Conclusion
Security orchestration is a critical component of modern cybersecurity, enabling organizations to automate and coordinate their security tools and processes. It offers numerous benefits, including improved threat detection and response, enhanced security visibility, reduced operational costs, and improved compliance. Security orchestration platforms integrate with various security tools and technologies, providing a centralized dashboard for managing security operations, automating workflows, and providing visibility into the security landscape.
Organizations should carefully consider their security needs, select the right platform, and integrate it effectively to maximize the benefits of security orchestration. By automating repetitive tasks, improving incident response capabilities, and providing a comprehensive view of the security landscape, security orchestration empowers organizations to proactively address security challenges and minimize the risk of security breaches.
Youtube Video:
