Security operations encompass the practices and processes employed to protect an organization’s assets from security breaches and cyberattacks. It involves continuous monitoring, analysis, and mitigation of security risks and vulnerabilities. Security operations teams work to detect, investigate, and respond to security incidents, as well as proactively identify and address potential threats.
Effective security operations are crucial for safeguarding an organization’s data, systems, and reputation. By implementing robust security measures and processes, organizations can protect themselves from financial losses, legal liabilities, and reputational damage that can result from security breaches.
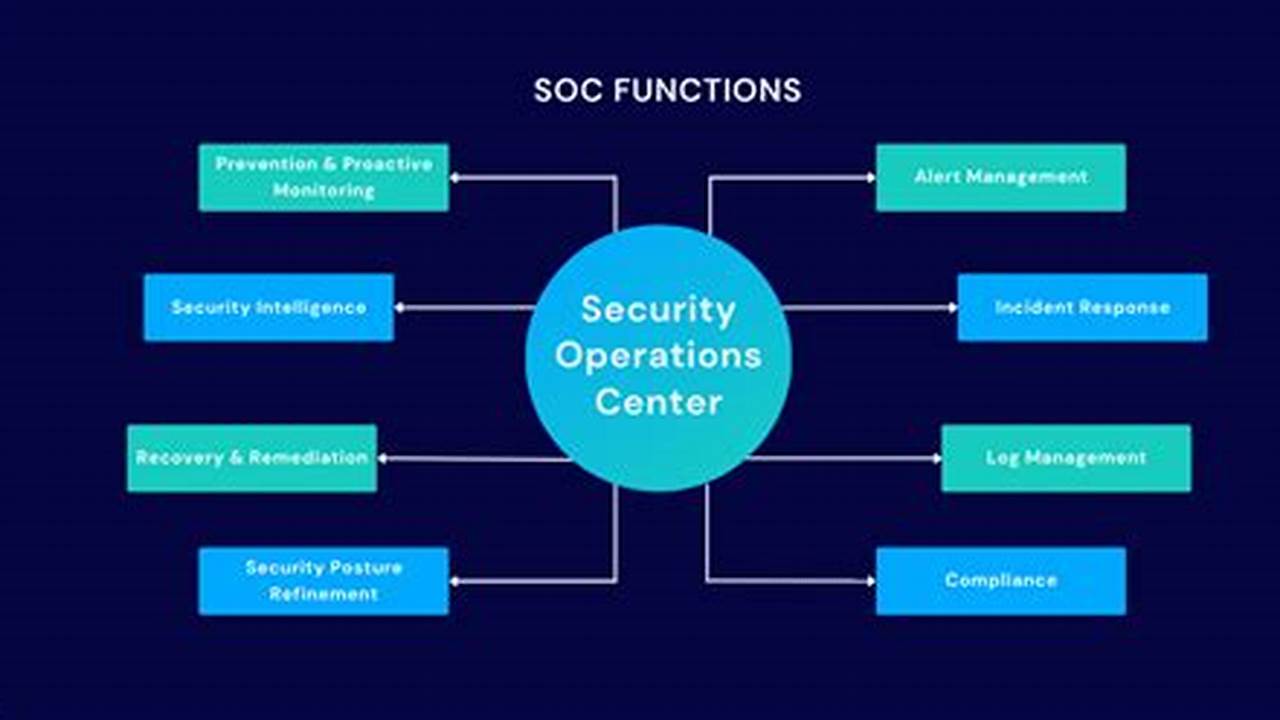
Security operations encompass a wide range of tasks, including:
- Security monitoring and analysis
- Incident detection and response
- Vulnerability management
- Security policy enforcement
- Security awareness training
Security operations
Security operations encompass a wide range of activities and processes that are essential for protecting an organization’s assets from security breaches and cyberattacks. Key aspects of security operations include:
- Monitoring and analysis: Continuously monitoring security logs and events to detect suspicious activity.
- Incident response: Responding to security incidents quickly and effectively to minimize damage.
- Vulnerability management: Identifying and patching vulnerabilities in software and systems.
- Policy enforcement: Ensuring that security policies are followed by all employees.
- Security awareness training: Educating employees about security risks and best practices.
- Threat intelligence: Gathering and analyzing information about potential threats to the organization.
- Risk management: Assessing and managing security risks to the organization.
- Compliance: Ensuring that the organization’s security practices comply with applicable laws and regulations.
These key aspects of security operations are essential for protecting an organization’s data, systems, and reputation. By implementing robust security measures and processes, organizations can protect themselves from financial losses, legal liabilities, and reputational damage that can result from security breaches.
Monitoring and analysis
Monitoring and analysis are critical components of security operations. By continuously monitoring security logs and events, organizations can detect suspicious activity and identify potential threats. This information can then be used to investigate security incidents, identify vulnerabilities, and take steps to mitigate risks.
For example, a security analyst might monitor security logs for failed login attempts. If a large number of failed login attempts are detected from a single IP address, this could indicate that an attacker is trying to brute-force their way into the network. The security analyst could then investigate the incident, block the IP address, and take steps to strengthen the organization’s password policy.
Monitoring and analysis are essential for protecting organizations from security breaches and cyberattacks. By continuously monitoring security logs and events, organizations can detect suspicious activity and take steps to mitigate risks.
Incident response
Incident response is a critical component of security operations. When a security incident occurs, it is essential to respond quickly and effectively to minimize damage. This involves taking steps to contain the incident, identify the root cause, and remediate the issue.
For example, if a server is compromised by a malware attack, the incident response team would work to isolate the server, identify the malware, and remove it from the system. The team would also work to identify the root cause of the attack and take steps to prevent similar attacks from occurring in the future.
Effective incident response requires a well-defined plan and a team of trained professionals. The incident response plan should outline the steps that should be taken in the event of a security incident, and the team should be trained to execute the plan quickly and effectively. Incident response is a vital part of security operations, and organizations that have a strong incident response plan and team are better prepared to mitigate the impact of security incidents.
Vulnerability management
Vulnerability management is a critical component of security operations. Vulnerabilities are weaknesses in software or systems that can be exploited by attackers to gain unauthorized access to data or systems. Identifying and patching vulnerabilities is essential for protecting organizations from security breaches and cyberattacks.
For example, a vulnerability in a web server could allow an attacker to execute arbitrary code on the server. This could give the attacker access to sensitive data, such as customer information or financial data. Patching the vulnerability would close the hole and prevent the attacker from exploiting it.
Effective vulnerability management requires a systematic approach. Organizations should regularly scan their systems for vulnerabilities, prioritize the most critical vulnerabilities, and patch them as soon as possible. Organizations should also implement a patch management process to ensure that patches are applied quickly and efficiently.
Vulnerability management is a vital part of security operations. By identifying and patching vulnerabilities, organizations can significantly reduce their risk of being compromised by a security breach or cyberattack.
Policy enforcement
Policy enforcement is a critical component of security operations. Security policies are designed to protect an organization’s assets from security breaches and cyberattacks. They outline the rules and procedures that employees must follow to maintain a secure environment. Ensuring that security policies are followed by all employees is essential for protecting the organization from security risks.
For example, a security policy might require employees to use strong passwords and to change their passwords regularly. This policy is designed to prevent attackers from guessing or cracking employee passwords and gaining access to the organization’s network. If employees do not follow this policy, the organization is at increased risk of a security breach.
Policy enforcement can be challenging, especially in large organizations with many employees. However, there are a number of tools and techniques that can be used to enforce security policies, such as:
- Security awareness training
- Technical controls
- Auditing and monitoring
Security awareness training educates employees about security risks and best practices. Technical controls can be used to enforce security policies, such as requiring employees to use strong passwords or to use a VPN when accessing the network remotely. Auditing and monitoring can be used to ensure that employees are following security policies and to identify any violations.
Policy enforcement is a vital part of security operations. By ensuring that security policies are followed by all employees, organizations can significantly reduce their risk of being compromised by a security breach or cyberattack.
Security awareness training
Security awareness training is a critical component of security operations. It educates employees about security risks and best practices, empowering them to protect the organization from security breaches and cyberattacks.
Employees are often the weakest link in the security chain. They may unwittingly click on malicious links, open phishing emails, or download malware that can compromise the organization’s network. Security awareness training can help to mitigate this risk by teaching employees how to identify and avoid these threats.
For example, security awareness training can teach employees about the importance of using strong passwords, not sharing their passwords with others, and being cautious about clicking on links in emails or on websites. Employees who are aware of the latest security threats are better equipped to protect themselves and the organization from cyberattacks.
Security awareness training is an essential part of a comprehensive security operations program. By educating employees about security risks and best practices, organizations can significantly reduce their risk of being compromised by a security breach or cyberattack.
Threat intelligence
Threat intelligence is a critical component of security operations. It involves gathering and analyzing information about potential threats to the organization, such as new vulnerabilities, malware, and attack methods. This information can then be used to develop and implement security measures to protect the organization from these threats.
-
Identifying new vulnerabilities
Threat intelligence can help organizations to identify new vulnerabilities in their systems and software. This information can then be used to patch the vulnerabilities and prevent attackers from exploiting them. -
Tracking malware
Threat intelligence can help organizations to track the latest malware threats. This information can then be used to develop and deploy anti-malware defenses to protect the organization’s systems from infection. -
Monitoring attack methods
Threat intelligence can help organizations to monitor the latest attack methods being used by attackers. This information can then be used to develop and implement security measures to protect the organization from these attacks. -
Predicting future threats
Threat intelligence can help organizations to predict future threats. This information can then be used to develop and implement security measures to protect the organization from these threats.
Threat intelligence is a vital part of security operations. By gathering and analyzing information about potential threats, organizations can develop and implement security measures to protect themselves from these threats.
Risk management
Risk management is the process of identifying, assessing, and managing security risks to an organization. It is a critical component of security operations, as it helps organizations to understand and mitigate the risks that could potentially harm their assets, reputation, or operations.
-
Identifying security risks
The first step in risk management is to identify the security risks that could potentially harm the organization. This can be done through a variety of methods, such as risk assessments, threat intelligence, and vulnerability scanning. -
Assessing security risks
Once the security risks have been identified, they need to be assessed to determine their likelihood and impact. This can be done using a variety of risk assessment methodologies, such as qualitative risk assessment or quantitative risk assessment. -
Managing security risks
Once the security risks have been assessed, they need to be managed to reduce their likelihood and impact. This can be done through a variety of risk management strategies, such as risk avoidance, risk mitigation, or risk transference. -
Monitoring security risks
The security risk landscape is constantly changing, so it is important to monitor security risks on an ongoing basis. This can be done through a variety of methods, such as security monitoring, threat intelligence, and vulnerability scanning.
Risk management is a complex and challenging process, but it is essential for organizations that want to protect their assets, reputation, and operations from security risks. By understanding and managing security risks, organizations can reduce their exposure to these risks and improve their overall security posture.
Compliance
Compliance is a critical component of security operations. It ensures that an organization’s security practices are in accordance with applicable laws and regulations. This is important for several reasons. First, compliance can help organizations to avoid legal penalties and fines. Second, it can help organizations to maintain a good reputation with customers and partners. Third, it can help organizations to attract and retain top talent.
There are a number of different laws and regulations that organizations must comply with, depending on their industry and location. Some of the most common include:
- The General Data Protection Regulation (GDPR)
- The Health Insurance Portability and Accountability Act (HIPAA)
- The Payment Card Industry Data Security Standard (PCI DSS)
- The Sarbanes-Oxley Act (SOX)
Organizations can comply with these laws and regulations by implementing a variety of security measures, such as:
- Encrypting data
- Implementing access controls
- Conducting regular security audits
- Providing security awareness training to employees
Compliance is an ongoing process. Organizations must continuously monitor their security practices to ensure that they are in compliance with applicable laws and regulations. They must also be prepared to make changes to their security practices as needed to address new threats and vulnerabilities.
By complying with applicable laws and regulations, organizations can protect themselves from legal penalties and fines, maintain a good reputation with customers and partners, and attract and retain top talent. Compliance is an essential component of security operations and should be a priority for all organizations.
Security Operations FAQs
Security operations is a critical function for any organization that wants to protect its assets and data from security breaches and cyberattacks. Security operations teams are responsible for monitoring and analyzing security logs and events, responding to security incidents, and managing security risks. They also work to ensure that the organization’s security practices comply with applicable laws and regulations.
Question 1: What is the difference between security operations and cybersecurity?
Security operations is a subset of cybersecurity that focuses on the day-to-day management and operation of security controls and processes. Cybersecurity, on the other hand, is a broader term that encompasses all aspects of protecting an organization’s assets and data from security threats.
Question 2: What are the key components of security operations?
The key components of security operations include security monitoring and analysis, incident response, vulnerability management, policy enforcement, security awareness training, threat intelligence, risk management, and compliance.
Question 3: What are the benefits of implementing effective security operations?
Effective security operations can help organizations to protect their assets and data from security breaches and cyberattacks, reduce their risk of legal penalties and fines, maintain a good reputation with customers and partners, and attract and retain top talent.
Question 4: What are the challenges of implementing effective security operations?
Organizations face a number of challenges when implementing effective security operations, including a shortage of skilled security professionals, the increasing complexity of security threats, and the need to comply with a growing number of laws and regulations.
Question 5: What are the trends in security operations?
The trends in security operations include the increasing use of artificial intelligence and machine learning, the adoption of cloud-based security solutions, and the growing importance of compliance.
Question 6: What is the future of security operations?
The future of security operations is bright. As the world becomes increasingly digital, organizations will need to invest more in security operations to protect their assets and data from security breaches and cyberattacks.
Summary of key takeaways or final thought:
Security operations is a critical function for any organization that wants to protect its assets and data from security breaches and cyberattacks. By implementing effective security operations, organizations can reduce their risk of legal penalties and fines, maintain a good reputation with customers and partners, and attract and retain top talent.
Transition to the next article section:
To learn more about security operations, please visit our website or contact us today.
Security Operations Tips
Security operations is a critical function for any organization that wants to protect its assets and data from security breaches and cyberattacks. By implementing effective security operations, organizations can reduce their risk of legal penalties and fines, maintain a good reputation with customers and partners, and attract and retain top talent.
Here are five tips for implementing effective security operations:
- Monitor and analyze security logs and events regularly. This will help you to identify suspicious activity and potential threats.
- Respond to security incidents quickly and effectively. This will help you to minimize the damage caused by a security breach.
- Manage security risks proactively. This will help you to reduce the likelihood of a security breach occurring in the first place.
- Comply with applicable laws and regulations. This will help you to avoid legal penalties and fines.
- Invest in security awareness training for employees. This will help to reduce the risk of a security breach caused by human error.
By following these tips, you can help to improve your organization’s security posture and protect your assets and data from security breaches and cyberattacks.
Transition to the article’s conclusion:
For more information on security operations, please visit our website.
Security Operations
Security operations are essential for protecting an organization’s assets and data from security breaches and cyberattacks. By implementing effective security operations, organizations can reduce their risk of legal penalties and fines, maintain a good reputation with customers and partners, and attract and retain top talent. Security operations encompass a wide range of activities, including security monitoring and analysis, incident response, vulnerability management, policy enforcement, security awareness training, threat intelligence, risk management, and compliance.
Organizations should take a proactive approach to security operations and invest in the necessary resources to protect their assets and data. By doing so, they can significantly reduce their risk of being compromised by a security breach or cyberattack.
Youtube Video: