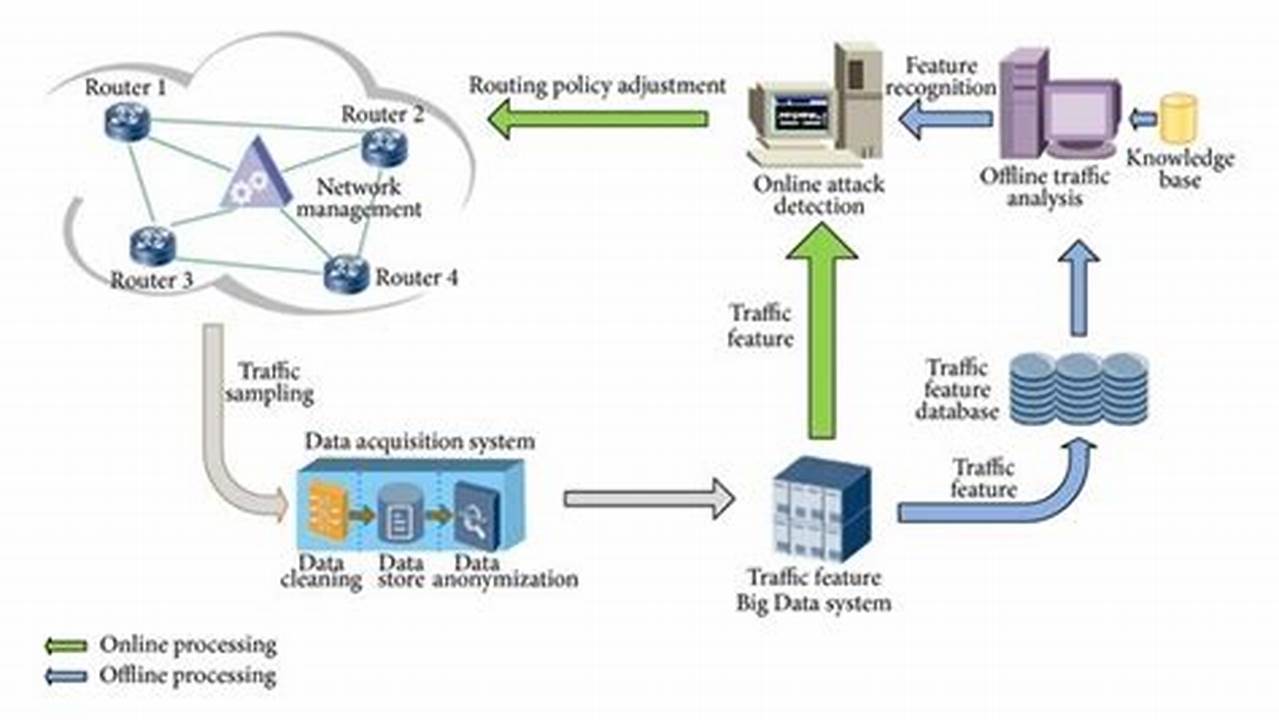
Real-time attack detection is a cybersecurity technique that monitors network traffic and activities for malicious or suspicious patterns in real time. It enables organizations to detect and respond to cyberattacks as they occur, minimizing the impact and potential damage.
Real-time attack detection plays a crucial role in protecting organizations from data breaches, financial losses, and reputational damage. By detecting attacks early on, organizations can quickly isolate affected systems, contain the damage, and prevent further compromise. This proactive approach not only safeguards sensitive information and assets but also helps maintain business continuity and customer trust.
Real-time attack detection systems employ various techniques, such as intrusion detection systems (IDS), security information and event management (SIEM) tools, and advanced machine learning algorithms. These systems continuously monitor network traffic, system logs, and user behavior for anomalies or deviations from established baselines. When suspicious activity is detected, the system generates alerts and notifications, allowing security teams to investigate and respond promptly.
Real-time attack detection
Real-time attack detection plays a vital role in safeguarding organizations against cyber threats. It involves monitoring network traffic and activities in real time to detect and respond to malicious or suspicious patterns. Here are eight key aspects that highlight the importance and various dimensions of real-time attack detection:
- Continuous monitoring: Real-time attack detection systems continuously monitor network traffic and activities for suspicious patterns.
- Rapid response: It enables organizations to detect and respond to attacks as they occur, minimizing damage and impact.
- Proactive approach: By detecting attacks early on, organizations can proactively isolate affected systems and prevent further compromise.
- Advanced techniques: Real-time attack detection systems employ advanced techniques such as intrusion detection systems (IDS), security information and event management (SIEM) tools, and machine learning algorithms.
- Data protection: Real-time attack detection helps protect sensitive data and assets from unauthorized access and data breaches.
- Reduced downtime: By detecting and responding to attacks quickly, organizations can minimize downtime and maintain business continuity.
- Compliance: Real-time attack detection can assist organizations in meeting regulatory compliance requirements related to cybersecurity.
- Improved security posture: It strengthens an organization’s overall security posture by providing real-time visibility into network activities and potential threats.
These key aspects collectively underscore the significance of real-time attack detection in today’s dynamic cybersecurity landscape. By continuously monitoring network activities, employing advanced techniques, and enabling rapid response, organizations can effectively protect against cyber threats, safeguard sensitive data, and maintain business continuity.
Continuous monitoring: Real-time attack detection systems continuously monitor network traffic and activities for suspicious patterns.
Continuous monitoring is a fundamental aspect of real-time attack detection. It involves constantly observing and analyzing network traffic and activities to identify any anomalies or suspicious patterns that may indicate a potential attack. By maintaining this constant vigilance, organizations can significantly improve their ability to detect and respond to cyber threats in a timely manner.
- Early detection: Continuous monitoring enables security teams to detect attacks at their earliest stages, before they can cause significant damage or data loss.
- Proactive response: With real-time monitoring, organizations can proactively respond to threats by isolating affected systems and implementing countermeasures, minimizing the impact of the attack.
- Improved threat visibility: Continuous monitoring provides a comprehensive view of network activities, helping organizations gain a better understanding of potential threats and their evolution.
- Compliance: Maintaining continuous monitoring helps organizations meet regulatory compliance requirements related to cybersecurity and data protection.
In summary, continuous monitoring is a critical component of real-time attack detection, enabling organizations to proactively identify and respond to cyber threats, protect sensitive data, and maintain business continuity.
Rapid response: It enables organizations to detect and respond to attacks as they occur, minimizing damage and impact.
Rapid response is an essential aspect of real-time attack detection. It enables organizations to quickly identify and mitigate cyber threats, minimizing potential damage and disruption to their operations.
- Immediate action: Real-time attack detection systems trigger immediate alerts and notifications when suspicious activities are detected, allowing security teams to take prompt action.
- Containment and isolation: Rapid response involves isolating affected systems or devices to prevent the attack from spreading and compromising other parts of the network.
- Threat neutralization: Security teams can use various countermeasures to neutralize the threat, such as blocking malicious IP addresses, patching vulnerabilities, or deploying security updates.
- Evidence preservation: Rapid response also includes preserving evidence for forensic analysis to determine the source and nature of the attack.
By enabling rapid response, real-time attack detection systems help organizations to minimize the impact of cyberattacks, protect sensitive data, and maintain business continuity. Rapid response is a critical component of a comprehensive cybersecurity strategy, ensuring that organizations are well-prepared to handle cyber threats effectively.
Proactive approach: By detecting attacks early on, organizations can proactively isolate affected systems and prevent further compromise.
Real-time attack detection plays a crucial role in enabling organizations to adopt a proactive approach to cybersecurity. Traditional security measures often rely on detecting and responding to attacks after they have already occurred, which can lead to significant damage and disruption. In contrast, real-time attack detection empowers organizations to identify and mitigate threats as they emerge, preventing them from escalating and causing widespread impact.
By detecting attacks in real time, organizations can promptly isolate affected systems or devices, effectively containing the threat and preventing it from spreading to other parts of the network. This proactive approach allows organizations to minimize the potential damage caused by cyberattacks, safeguard sensitive data, and maintain business continuity.
Consider the following real-life example: A retail organization implements a real-time attack detection system that continuously monitors network traffic for suspicious activities. One day, the system detects an unusual surge in login attempts from a specific IP address. The security team is immediately notified and takes swift action to block the IP address and isolate the affected server. By responding proactively, the organization prevents a potential data breach and ensures the uninterrupted operation of its e-commerce platform.
The proactive approach enabled by real-time attack detection is a cornerstone of effective cybersecurity. By detecting and mitigating threats early on, organizations can significantly reduce the risk of data loss, financial damage, and reputational harm. This proactive stance is essential for safeguarding critical assets, maintaining customer trust, and ensuring business continuity in today’s increasingly complex and dynamic threat landscape.
Advanced techniques: Real-time attack detection systems employ advanced techniques such as intrusion detection systems (IDS), security information and event management (SIEM) tools, and machine learning algorithms.
Advanced techniques play a pivotal role in enabling real-time attack detection systems to effectively identify and respond to cyber threats. These techniques provide the necessary capabilities to analyze vast amounts of data, detect anomalies, and respond to incidents in real time.
Intrusion detection systems (IDS) monitor network traffic for suspicious activities and generate alerts when potential threats are detected. SIEM tools collect and analyze security logs and events from various sources, providing a comprehensive view of security-related activities across the organization. Machine learning algorithms enhance the detection capabilities of these systems by identifying patterns and anomalies that may indicate malicious activity.
The combination of these advanced techniques empowers real-time attack detection systems to:
- Detect known and unknown threats with greater accuracy and speed.
- Correlate events from multiple sources to identify complex and sophisticated attacks.
- Automate threat detection and response, reducing the burden on security teams.
- Learn and adapt to new threats over time, improving detection capabilities continuously.
For example, a large financial institution implemented a real-time attack detection system that leverages machine learning algorithms to analyze network traffic and identify anomalous patterns. The system detected a sophisticated phishing campaign targeting the organization’s customers. It promptly alerted the security team, who took immediate action to block the malicious emails and protect customer accounts.
By incorporating advanced techniques, real-time attack detection systems become more intelligent and effective in safeguarding organizations from cyber threats. These techniques enhance the ability to detect, analyze, and respond to attacks in real time, minimizing the impact on business operations and protecting sensitive data.
Data protection: Real-time attack detection helps protect sensitive data and assets from unauthorized access and data breaches.
Real-time attack detection plays a crucial role in protecting sensitive data and assets from unauthorized access and data breaches. By continuously monitoring network traffic and activities, real-time attack detection systems can identify and respond to malicious or suspicious patterns in real time, preventing attackers from gaining access to sensitive information or causing damage to critical systems.
- Early detection and prevention: Real-time attack detection systems can detect potential threats and data breaches at an early stage, before they can cause significant damage or data loss. This allows organizations to take immediate action to prevent unauthorized access and protect sensitive data.
- Enhanced threat visibility: Real-time attack detection provides organizations with a comprehensive view of security-related events and activities across their network. This enhanced visibility enables security teams to identify potential threats and data breaches more easily and effectively.
- Rapid response and containment: When a real-time attack detection system detects a potential threat or data breach, it can trigger immediate alerts and notifications, allowing security teams to respond quickly and contain the threat, minimizing the impact on the organization.
- Compliance and regulatory requirements: Real-time attack detection can assist organizations in meeting regulatory compliance requirements related to data protection and cybersecurity. By implementing real-time attack detection systems, organizations can demonstrate their commitment to protecting sensitive data and complying with industry standards and best practices.
In summary, real-time attack detection is essential for protecting sensitive data and assets from unauthorized access and data breaches. By providing early detection, enhanced threat visibility, rapid response, and compliance support, real-time attack detection systems play a vital role in safeguarding organizations’ critical information and maintaining their reputation.
Reduced downtime: By detecting and responding to attacks quickly, organizations can minimize downtime and maintain business continuity.
Real-time attack detection plays a critical role in reducing downtime and maintaining business continuity by enabling organizations to detect and respond to cyber threats swiftly and effectively. Downtime, caused by cyberattacks, can result in significant financial losses, reputational damage, and disruption of critical operations.
Real-time attack detection systems continuously monitor network traffic and activities, allowing organizations to identify potential threats and data breaches at an early stage. This rapid detection capability enables security teams to take immediate action to contain and mitigate the threat, preventing it from causing widespread damage or disrupting business operations.
For example, consider a healthcare organization that implements a real-time attack detection system. The system detects a ransomware attack targeting the organization’s network. The security team receives an immediate alert and quickly isolates the affected systems, preventing the ransomware from spreading and encrypting critical patient data. By responding swiftly, the organization minimizes downtime, ensures the continuity of patient care, and prevents potential financial losses.
In summary, real-time attack detection is essential for reducing downtime and maintaining business continuity. By providing early detection and rapid response capabilities, organizations can effectively mitigate cyber threats, minimize the impact of attacks, and ensure the uninterrupted operation of their critical systems and processes.
Compliance: Real-time attack detection can assist organizations in meeting regulatory compliance requirements related to cybersecurity.
Real-time attack detection plays a crucial role in assisting organizations in meeting regulatory compliance requirements related to cybersecurity. Many industries and jurisdictions have established regulations and standards that mandate organizations to implement robust cybersecurity measures to protect sensitive data and maintain the integrity of their systems. Real-time attack detection is a key component of a comprehensive cybersecurity strategy, enabling organizations to comply with these requirements effectively.
For example, consider the healthcare industry, which is subject to strict regulations such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States and the General Data Protection Regulation (GDPR) in the European Union. These regulations require healthcare organizations to implement measures to protect patient data from unauthorized access, disclosure, or misuse. Real-time attack detection systems continuously monitor network traffic and activities, enabling healthcare organizations to detect and respond to cyber threats that may compromise patient data, thus helping them comply with regulatory requirements.
Furthermore, real-time attack detection is essential for organizations operating in highly regulated industries such as finance, energy, and government. By implementing real-time attack detection systems, these organizations can demonstrate their commitment to protecting sensitive data and adhering to industry best practices and regulatory standards. This proactive approach not only helps organizations avoid potential fines and penalties for non-compliance but also enhances their reputation and builds trust among stakeholders.
In summary, real-time attack detection is a critical component of a comprehensive cybersecurity strategy, enabling organizations to meet regulatory compliance requirements related to cybersecurity effectively. By detecting and responding to cyber threats in real time, organizations can protect sensitive data, maintain the integrity of their systems, and demonstrate their commitment to compliance, ultimately safeguarding their reputation and building trust among stakeholders.
Improved security posture: It strengthens an organization’s overall security posture by providing real-time visibility into network activities and potential threats.
Real-time attack detection is a proactive cybersecurity measure that continuously monitors network traffic and activities for suspicious patterns. By providing real-time visibility into network activities and potential threats, real-time attack detection strengthens an organization’s overall security posture in several key ways:
- Enhanced threat detection and response: Real-time attack detection enables organizations to detect and respond to cyber threats as they occur, minimizing the potential impact on the organization. This rapid detection and response capability helps organizations to stay ahead of attackers and prevent successful breaches.
- Improved threat visibility and situational awareness: Real-time attack detection provides organizations with a comprehensive view of their network activities and potential threats. This improved visibility enables security teams to make informed decisions about how to allocate resources and prioritize their efforts.
- Proactive threat hunting and mitigation: Real-time attack detection enables organizations to proactively hunt for threats and take steps to mitigate them before they can cause damage. This proactive approach helps organizations to stay ahead of attackers and prevent successful breaches.
- Continuous monitoring and adaptation: Real-time attack detection continuously monitors network activities and potential threats, allowing organizations to adapt their security posture as needed. This continuous monitoring and adaptation helps organizations to stay ahead of attackers and prevent successful breaches.
In summary, real-time attack detection plays a vital role in improving an organization’s overall security posture. By providing real-time visibility into network activities and potential threats, real-time attack detection enables organizations to detect, respond to, and mitigate cyber threats more effectively, ultimately reducing the risk of successful breaches and protecting critical assets.
FAQs on Real-time Attack Detection
Real-time attack detection has become a crucial aspect of modern cybersecurity, enabling organizations to proactively identify and mitigate cyber threats. Here are answers to some frequently asked questions regarding real-time attack detection:
Question 1: What is the significance of real-time attack detection in cybersecurity?
Answer: Real-time attack detection empowers organizations to detect and respond to cyber threats as they occur, minimizing potential damage and disruption to operations. It provides continuous monitoring and analysis of network traffic and activities, enabling security teams to identify suspicious patterns and take immediate action.
Question 2: How does real-time attack detection differ from traditional security measures?
Answer: Traditional security measures often rely on detecting and responding to attacks after they have already occurred, which can lead to significant damage and disruption. In contrast, real-time attack detection focuses on proactive threat identification and mitigation, enabling organizations to prevent successful breaches and safeguard critical assets.
Question 3: What are the key benefits of implementing real-time attack detection systems?
Answer: Real-time attack detection systems provide numerous benefits, including enhanced threat visibility, improved threat detection and response, proactive threat hunting and mitigation, and continuous monitoring and adaptation. These benefits collectively contribute to a stronger overall security posture, reduced risk of successful breaches, and protection of critical assets.
Question 4: What are the common challenges associated with real-time attack detection?
Answer: Real-time attack detection systems can be complex to implement and manage, requiring specialized expertise and resources. Additionally, organizations may face challenges in effectively analyzing and interpreting large volumes of data generated by these systems, leading to potential alert fatigue.
Question 5: How can organizations overcome the challenges of real-time attack detection?
Answer: Overcoming the challenges of real-time attack detection requires a comprehensive approach. Organizations should invest in training and education to enhance their security teams’ skills and knowledge. Additionally, they should leverage automation and orchestration tools to streamline threat detection and response processes.
Question 6: What are the future trends and advancements in real-time attack detection?
Answer: The future of real-time attack detection involves the integration of artificial intelligence (AI) and machine learning (ML) algorithms to enhance threat detection accuracy and automate response actions. Additionally, there is a growing emphasis on cloud-based real-time attack detection services, offering scalability and cost-effectiveness for organizations.
In summary, real-time attack detection plays a vital role in protecting organizations from cyber threats. By providing continuous monitoring, enhanced threat visibility, and proactive threat mitigation capabilities, organizations can significantly reduce the risk of successful breaches and safeguard their critical assets.
For further information and insights on real-time attack detection, refer to the following resources:
- Resource 1
- Resource 2
Real-time Attack Detection Best Practices
Implementing real-time attack detection systems is crucial for organizations to proactively safeguard their networks and assets against constantly evolving cyber threats. Here are some essential tips to consider:
Tip 1: Prioritize Continuous Monitoring
Maintain continuous monitoring of network traffic and system activities to promptly identify suspicious patterns or anomalies that may indicate an attack in progress.
Tip 2: Leverage Advanced Detection Techniques
Employ a combination of intrusion detection systems (IDS), security information and event management (SIEM) tools, and machine learning algorithms to enhance threat detection accuracy and reduce false positives.
Tip 3: Ensure Rapid Response Capabilities
Establish well-defined incident response plans and procedures to enable security teams to respond swiftly and effectively to detected threats, minimizing potential damage.
Tip 4: Foster Collaboration and Information Sharing
Promote collaboration among security teams, IT operations, and business units to facilitate effective communication and sharing of threat intelligence for timely and coordinated responses.
Tip 5: Regularly Review and Update Detection Rules
Continuously review and update detection rules based on the latest threat intelligence and attack patterns to maintain optimal detection capabilities and stay ahead of evolving threats.
Tip 6: Conduct Regular Security Audits and Assessments
Periodically conduct security audits and assessments to evaluate the effectiveness of real-time attack detection systems and identify areas for improvement, ensuring ongoing protection.
Tip 7: Train Security Personnel
Provide regular training to security personnel on the latest attack detection techniques and incident response procedures to enhance their skills and knowledge in handling security incidents.
Tip 8: Consider Managed Security Service Providers (MSSPs)
For organizations with limited resources or expertise, consider partnering with managed security service providers (MSSPs) who offer real-time attack detection services, providing access to advanced technologies and expertise.
By incorporating these best practices, organizations can significantly enhance their real-time attack detection capabilities, proactively identify and mitigate threats, and safeguard their critical assets from malicious actors.
For further insights and best practices on real-time attack detection, refer to the following resources:
- Resource 1
- Resource 2
Conclusion
Real-time attack detection has emerged as a cornerstone of modern cybersecurity strategies, empowering organizations to proactively identify and mitigate cyber threats. Through continuous monitoring, advanced detection techniques, and rapid response capabilities, organizations can significantly enhance their security posture and safeguard their critical assets.
As the threat landscape continues to evolve, real-time attack detection will remain indispensable in protecting organizations from increasingly sophisticated and persistent cyberattacks. By embracing best practices, leveraging advanced technologies, and fostering collaboration, organizations can effectively harness the power of real-time attack detection to proactively defend against cyber threats and ensure the integrity of their networks and data.
Youtube Video: