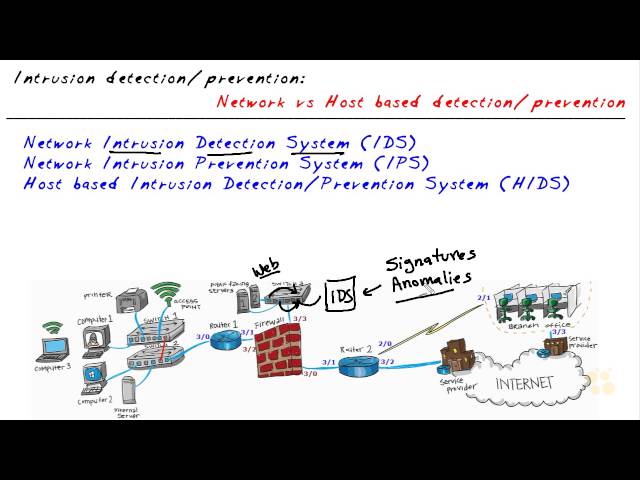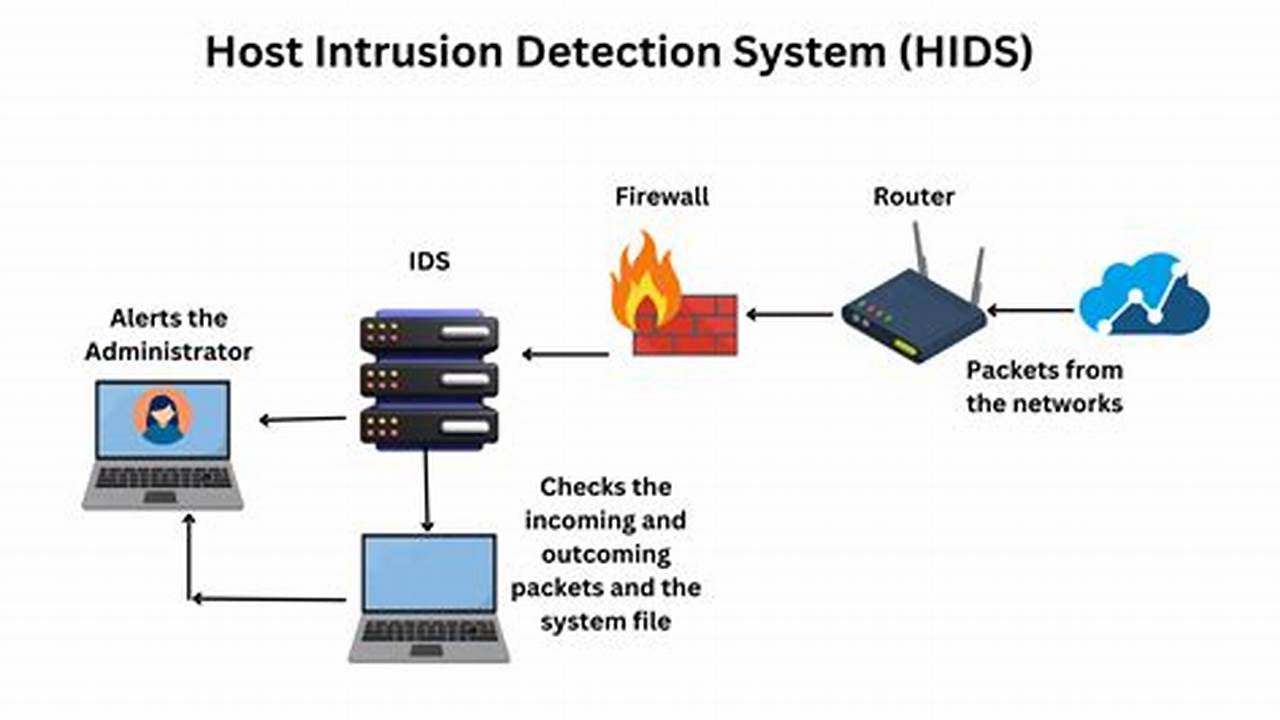
Host intrusion detection systems (HIDSs) monitor a host computer or network for suspicious activity. They can detect a variety of attacks, including unauthorized access, file modifications, and privilege escalation. HIDSs use a variety of techniques to detect attacks, including file integrity monitoring, process monitoring, and network traffic analysis.
HIDSs are an important part of a comprehensive security strategy. They can help to protect against a wide range of attacks and can provide early warning of security breaches. HIDSs have been used for many years and have a proven track record of success.
The main topics covered in this article include:
- What is host intrusion detection?
- How does host intrusion detection work?
- What are the benefits of host intrusion detection?
- What are the challenges of host intrusion detection?
- How to choose a host intrusion detection system
Host intrusion detection
Host intrusion detection systems (HIDSs) are an important part of a comprehensive security strategy. They can help to protect against a wide range of attacks and can provide early warning of security breaches.
- Detection methods: File integrity monitoring, process monitoring, network traffic analysis
- Benefits: Real-time monitoring, threat detection, incident response
- Challenges: False positives, resource-intensive, skilled personnel
- Types: Agent-based, agentless, network-based
- Use cases: Critical infrastructure, financial institutions, healthcare organizations
- Trends: Machine learning, artificial intelligence, cloud-based solutions
These key aspects provide a comprehensive overview of host intrusion detection. By understanding these aspects, organizations can make informed decisions about how to implement and manage HIDSs to protect their networks and data.
Detection methods
Host intrusion detection (HIDS) systems rely on a variety of detection methods to identify suspicious activity and potential threats. These methods include file integrity monitoring, process monitoring, and network traffic analysis.
File integrity monitoring (FIM) tracks changes to critical system files and applications. By comparing the current state of a file to a known good baseline, FIM can detect unauthorized modifications that may indicate an attack. For instance, if an attacker modifies a system binary to gain elevated privileges, FIM can identify the change and alert the security team.
Process monitoring tracks the behavior of running processes. It can detect suspicious activity, such as processes that attempt to access unauthorized resources or execute malicious code. Process monitoring can also identify processes that consume excessive resources, which may indicate a denial-of-service (DoS) attack.
Network traffic analysis (NTA) monitors network traffic for suspicious patterns and anomalies. It can detect attacks such as port scans, malicious traffic, and data exfiltration. NTA can also identify compromised hosts that are communicating with external command-and-control (C&C) servers.
These detection methods are essential for HIDSs to provide comprehensive protection against a wide range of attacks. By combining these methods, HIDSs can effectively detect and respond to threats in real time.
Benefits
Host intrusion detection (HIDS) systems offer significant benefits in terms of real-time monitoring, threat detection, and incident response. These capabilities are crucial for organizations to protect their networks and data from a wide range of attacks.
- Real-time monitoring: HIDSs continuously monitor host systems for suspicious activity and potential threats. This allows organizations to detect attacks in real time and respond quickly to minimize damage.
- Threat detection: HIDSs use a variety of detection methods to identify known and unknown threats. This includes detecting unauthorized access, file modifications, and malicious code execution.
- Incident response: HIDSs can be integrated with other security tools and systems to automate incident response. This can help organizations to quickly contain and mitigate threats, reducing the impact of attacks.
The benefits of HIDSs are essential for organizations to maintain a strong security posture. By providing real-time monitoring, threat detection, and incident response capabilities, HIDSs help organizations to protect their networks and data from a wide range of attacks.
Challenges
Host intrusion detection (HIDS) systems are essential for protecting networks and data from a wide range of threats. However, they also come with a number of challenges, including false positives, resource intensiveness, and the need for skilled personnel.
- False positives: HIDSs can sometimes generate false positives, which are alerts that indicate a potential threat when there is actually no threat present. This can lead to wasted time and resources investigating and responding to non-existent threats.
- Resource intensiveness: HIDSs can be resource-intensive, especially on large networks with a high volume of traffic. This can slow down system performance and impact the overall efficiency of the network.
- Skilled personnel: HIDSs require skilled personnel to install, configure, and maintain. This can be a challenge for organizations that do not have the in-house expertise or resources to support HIDSs.
Despite these challenges, HIDSs remain an essential part of a comprehensive security strategy. By understanding the challenges involved, organizations can take steps to mitigate them and ensure that their HIDSs are effective in protecting their networks and data.
Types
Host intrusion detection (HIDS) systems come in three main types: agent-based, agentless, and network-based. Each type has its own advantages and disadvantages, and the best type for a particular organization will depend on its specific needs and environment.
Agent-based HIDSs use software agents that are installed on each host system. These agents monitor the system for suspicious activity and report any findings to a central management console. Agent-based HIDSs are very effective at detecting threats, but they can be resource-intensive and difficult to manage on large networks.
Agentless HIDSs do not use software agents. Instead, they monitor the network for suspicious traffic and activity. Agentless HIDSs are less resource-intensive than agent-based HIDSs, but they are not as effective at detecting threats.
Network-based HIDSs monitor the network for suspicious traffic and activity. They can be used to detect attacks that are targeting the network itself, as well as attacks that are targeting individual hosts on the network. Network-based HIDSs are less effective at detecting threats than agent-based HIDSs, but they are more scalable and easier to manage.
The type of HIDS that is best for a particular organization will depend on its specific needs and environment. Organizations with large networks may want to consider using a network-based HIDS, while organizations with smaller networks may want to consider using an agent-based HIDS. Organizations that are concerned about resource consumption may want to consider using an agentless HIDS.
Use cases
Host intrusion detection (HIDS) systems are essential for protecting critical infrastructure, financial institutions, and healthcare organizations from a wide range of threats. These organizations rely on their IT systems to provide critical services, and any disruption to these systems could have a devastating impact.
- Critical infrastructure: HIDSs can help to protect critical infrastructure, such as power plants, water treatment facilities, and transportation systems, from cyber attacks. These attacks could cause widespread disruption and even loss of life.
- Financial institutions: HIDSs can help to protect financial institutions from fraud and other cyber crimes. These crimes could result in the loss of millions of dollars and damage the reputation of the institution.
- Healthcare organizations: HIDSs can help to protect healthcare organizations from cyber attacks that could compromise patient data or disrupt the delivery of healthcare services. These attacks could put patients at risk and damage the reputation of the organization.
HIDSs are an essential part of a comprehensive security strategy for critical infrastructure, financial institutions, and healthcare organizations. By detecting and responding to threats in real time, HIDSs can help to protect these organizations from a wide range of cyber attacks.
Trends
Machine learning, artificial intelligence (AI), and cloud-based solutions are playing an increasingly important role in host intrusion detection (HIDS). These technologies can help HIDS systems to detect threats more accurately and efficiently, and to respond to threats more quickly and effectively.
Machine learning can be used to train HIDS systems to identify new and unknown threats. Machine learning algorithms can learn from historical data to identify patterns of activity that are associated with malicious behavior. This allows HIDS systems to detect threats that are not known to the system administrator or security analyst.
Artificial intelligence can be used to automate the process of threat detection and response. AI-powered HIDS systems can use machine learning algorithms to identify threats, and then use AI techniques to determine the best course of action to take. This can help organizations to respond to threats more quickly and effectively.
Cloud-based solutions can be used to deliver HIDS services on a pay-as-you-go basis. This can make it easier for organizations to implement and manage HIDS systems, and can also help to reduce the cost of HIDS.
The combination of machine learning, artificial intelligence, and cloud-based solutions is helping to make HIDS systems more effective and easier to use. As these technologies continue to develop, HIDS systems will become even more essential for protecting organizations from cyber threats.
Host Intrusion Detection FAQs
This section addresses frequently asked questions (FAQs) about host intrusion detection (HIDS) to provide a comprehensive understanding of the topic.
Question 1: What is host intrusion detection (HIDS)?
Answer: HIDS is a security mechanism that monitors a host system or network for suspicious activities and potential threats. It employs various detection techniques to identify unauthorized access, file modifications, and other malicious behaviors.
Question 2: How does HIDS differ from network intrusion detection systems (NIDS)?
Answer: HIDS monitors individual hosts or endpoints, while NIDS focuses on network traffic analysis. HIDS provides a more granular level of protection by detecting threats within the host system itself.
Question 3: What are the benefits of using HIDS?
Answer: HIDS offers real-time monitoring, threat detection, and incident response capabilities. It helps organizations safeguard their systems by identifying and mitigating security breaches.
Question 4: What are the challenges associated with HIDS implementation?
Answer: HIDS can generate false positives, consume system resources, and require skilled personnel for operation. It’s crucial to address these challenges to ensure effective HIDS deployment.
Question 5: What are the different types of HIDS?
Answer: HIDS can be agent-based, agentless, or network-based. Each type has its advantages and is suitable for different environments.
Question 6: How is HIDS evolving with new technologies?
Answer: Machine learning, artificial intelligence, and cloud-based solutions are enhancing HIDS capabilities by improving threat detection accuracy, automating response actions, and simplifying deployment.
These FAQs provide a foundational understanding of HIDS, its benefits, challenges, types, and ongoing advancements. By leveraging HIDS effectively, organizations can strengthen their security posture and protect against a wide range of cyber threats.
Transition to the next article section: Understanding the different types of HIDS and their applications
Host Intrusion Detection Tips
Implementing host intrusion detection (HIDS) is crucial for safeguarding your systems against malicious activities. Here are several tips to optimize your HIDS deployment:
Tip 1: Choose the Right HIDS Type
Select the HIDS type that aligns with your environment, whether agent-based, agentless, or network-based. Each type offers unique advantages and is suited for different scenarios.
Tip 2: Focus on Essential System Files
Prioritize monitoring critical system files and applications to detect unauthorized modifications promptly. This helps identify potential threats that could compromise your system’s integrity.
Tip 3: Leverage Machine Learning
Incorporate machine learning algorithms into your HIDS to enhance threat detection accuracy. Machine learning models can identify new and evolving threats, providing proactive protection.
Tip 4: Set Up Real-Time Alerts
Configure your HIDS to generate real-time alerts for suspicious activities. This enables prompt response and containment of potential threats, minimizing their impact on your system.
Tip 5: Regularly Review and Update Rules
Periodically review and update your HIDS rules to ensure they remain effective against the latest threats. Outdated rules can hinder HIDS’s ability to detect and respond to emerging threats.
Tip 6: Integrate with Other Security Tools
Integrate your HIDS with other security tools, such as firewalls and antivirus software, to enhance overall security. This comprehensive approach provides multiple layers of protection against cyber threats.
Tip 7: Train Your Team
Educate your team on HIDS best practices and incident response procedures. Empowering your staff with the necessary knowledge ensures effective HIDS management and timely threat mitigation.
Summary:
By following these tips, you can optimize your HIDS deployment, strengthen your security posture, and proactively protect your systems from malicious threats.
Host Intrusion Detection
In conclusion, host intrusion detection (HIDS) plays a vital role in protecting systems from malicious activities and cyber threats. This article has explored the different aspects of HIDS, including its detection methods, benefits, challenges, and types. We have discussed the significance of HIDS in critical sectors such as infrastructure, finance, and healthcare.
As technology advances, HIDS continues to evolve with machine learning, artificial intelligence, and cloud-based solutions. These advancements enhance threat detection accuracy, automate response actions, and simplify deployment. Organizations must embrace these innovations to strengthen their security posture and stay ahead of emerging threats.
Youtube Video: