Essential Endpoint Defense and Response Strategies for Enhanced Cybersecurity
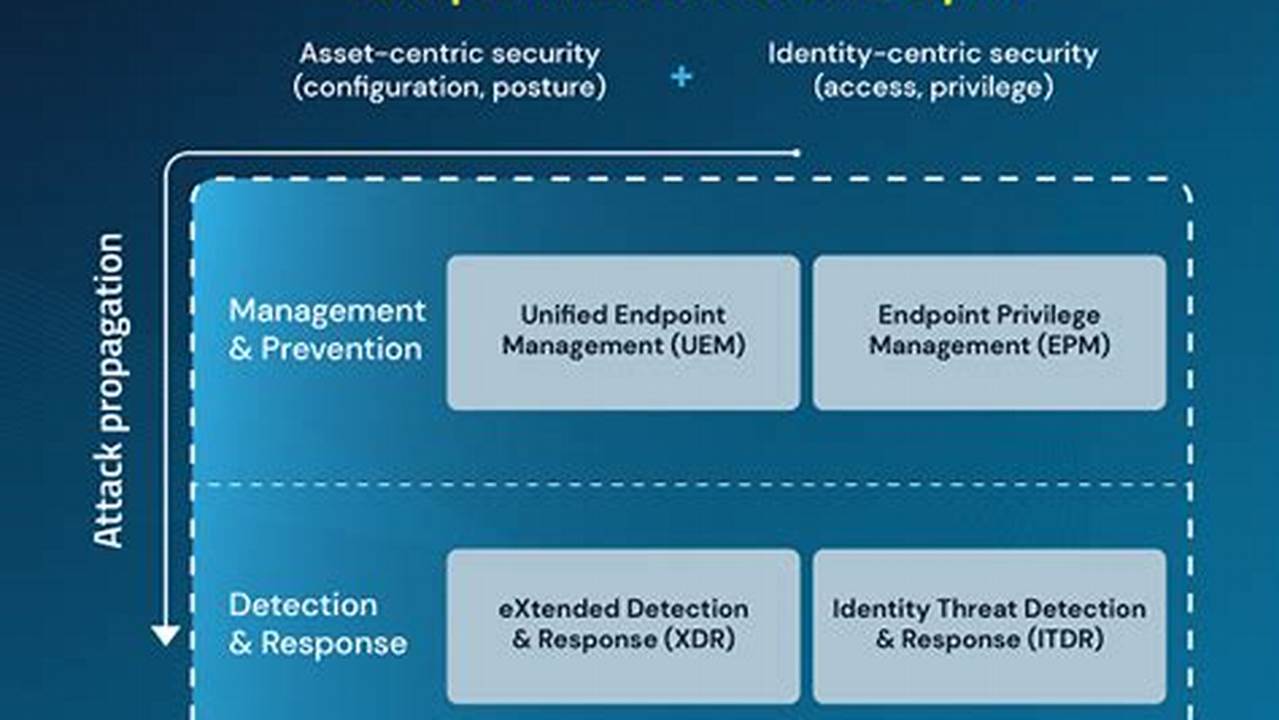
Endpoint defense and response encompasses security measures designed to protect endpoints, such as laptops, desktops, and mobile devices, from cyber threats. It involves detecting, preventing, and responding to malicious activities targeting these endpoints. Endpoint security solutions typically include features like antivirus and anti-malware protection, intrusion detection and prevention systems (IDS/IPS), and endpoint detection and response (EDR) capabilities.
Endpoint defense and response is crucial for safeguarding organizations from the growing sophistication and frequency of cyberattacks. By implementing robust endpoint security measures, organizations can reduce the risk of data breaches, financial losses, and reputational damage. Endpoint security solutions provide real-time monitoring, threat detection, and automated response mechanisms, enabling organizations to swiftly identify and mitigate security incidents.
In recent years, endpoint defense and response has become increasingly important due to the rise of remote work and the proliferation of Internet of Things (IoT) devices. With more endpoints connecting to corporate networks, organizations need comprehensive security solutions to protect against vulnerabilities and potential entry points for cybercriminals. Endpoint defense and response plays a vital role in maintaining a strong security posture and ensuring business continuity in the face of evolving cyber threats.
Endpoint defense and response
Endpoint defense and response is a critical aspect of cybersecurity, involving measures to protect endpoints such as laptops, desktops, and mobile devices from cyber threats. It encompasses various dimensions, including:
- Prevention: Implementing security measures to prevent malicious activity from reaching endpoints.
- Detection: Using tools and techniques to identify and monitor suspicious activity on endpoints.
- Response: Taking appropriate actions to contain and mitigate security incidents on endpoints.
- Visibility: Gaining insights into endpoint activities and security posture to improve threat detection and response.
- Automation: Utilizing automated tools and processes to streamline endpoint security tasks and improve efficiency.
- Integration: Connecting endpoint security solutions with other security tools and platforms for comprehensive threat protection.
These key aspects are interconnected and essential for effective endpoint defense and response. By implementing robust endpoint security measures, organizations can significantly reduce the risk of data breaches, financial losses, and reputational damage. Endpoint defense and response plays a vital role in maintaining a strong security posture and ensuring business continuity in the face of evolving cyber threats.
Prevention
Prevention is a critical component of endpoint defense and response, as it focuses on implementing security measures to proactively block malicious activity from reaching endpoints in the first place. This involves deploying a range of security controls and technologies, such as firewalls, intrusion detection and prevention systems (IDS/IPS), antivirus and anti-malware software, and access control mechanisms.
Effective prevention measures are essential for reducing the risk of successful cyberattacks. By preventing malicious activity from reaching endpoints, organizations can significantly reduce the likelihood of data breaches, financial losses, and reputational damage. Prevention measures also help to minimize the workload for detection and response teams, as there are fewer incidents to investigate and mitigate.
One of the key challenges in prevention is staying ahead of the evolving tactics and techniques used by cybercriminals. Attackers are constantly developing new ways to bypass security controls and exploit vulnerabilities in endpoints. Therefore, it is important for organizations to continuously update and refine their prevention measures, and to invest in security awareness training for employees.
Prevention is a vital part of a comprehensive endpoint defense and response strategy. By implementing robust prevention measures, organizations can significantly reduce the risk of cyberattacks and protect their valuable data and assets.
Detection
Detection is a critical component of endpoint defense and response, as it enables organizations to identify and monitor suspicious activity on endpoints, allowing them to respond quickly and effectively to potential threats. Detection involves the use of a variety of tools and techniques, such as:
- Intrusion detection systems (IDS) and intrusion prevention systems (IPS): IDS and IPS monitor network traffic and system activity for suspicious patterns or behaviors that may indicate an attack. They can be configured to alert administrators or automatically block malicious activity.
- Antivirus and anti-malware software: Antivirus and anti-malware software scans files and applications for known malicious code and threats. They can also monitor system behavior for suspicious activity and prevent the execution of malicious code.
- Endpoint detection and response (EDR) solutions: EDR solutions provide real-time visibility into endpoint activity and can detect and respond to suspicious behavior, such as fileless attacks, lateral movement, and ransomware.
- Security information and event management (SIEM) systems: SIEM systems collect and analyze security logs from endpoints and other security devices to identify patterns and trends that may indicate an attack.
Effective detection capabilities are essential for endpoint defense and response, as they enable organizations to identify and respond to threats before they can cause significant damage. Detection tools and techniques should be regularly updated and tuned to ensure that they can identify the latest threats and attack techniques.
Response
Response is a critical component of endpoint defense and response, as it involves taking appropriate actions to contain and mitigate security incidents on endpoints. This includes identifying the scope and nature of the incident, containing the damage, and taking steps to prevent further compromise. Response activities may vary depending on the type of security incident, but typically involve the following steps:
- Incident identification and assessment: Identifying the type of security incident, its scope, and potential impact on the organization.
- Containment: Taking steps to contain the incident and prevent it from spreading, such as isolating infected endpoints or blocking malicious network traffic.
- Eradication: Removing the malicious code or threat from infected endpoints and restoring them to a clean state.
- Recovery: Restoring affected systems and data to a normal state of operation, including restoring lost data and reconfiguring systems.
- Follow-up and reporting: Documenting the incident, analyzing its root cause, and implementing measures to prevent similar incidents in the future.
Effective response capabilities are essential for endpoint defense and response, as they enable organizations to minimize the impact of security incidents and restore normal operations as quickly as possible. Response plans should be developed and tested in advance, and response teams should be trained to respond quickly and efficiently to security incidents.
Visibility
Visibility is a critical aspect of endpoint defense and response, as it provides organizations with the insights they need to improve threat detection and response capabilities. By gaining visibility into endpoint activities and security posture, organizations can identify potential threats and vulnerabilities, prioritize their response efforts, and take proactive steps to prevent and mitigate security incidents.
- Endpoint monitoring and telemetry: Endpoint monitoring tools collect and analyze data on endpoint activities, such as file access, process execution, and network connections. This data can be used to detect suspicious behavior, identify potential threats, and investigate security incidents. Telemetry data from endpoints can also be used to improve the effectiveness of threat detection and response tools, such as IDS/IPS and EDR solutions.
- Security posture assessment: Security posture assessment tools evaluate the security posture of endpoints by identifying vulnerabilities, misconfigurations, and compliance gaps. This information can be used to prioritize remediation efforts and improve the overall security posture of the organization. Regular security posture assessments can also help organizations identify trends and patterns that may indicate potential threats.
- Threat intelligence: Threat intelligence provides organizations with information about the latest threats and attack techniques. This information can be used to update detection and response tools, and to develop proactive measures to prevent and mitigate security incidents. Sharing threat intelligence with other organizations can also help to improve the overall security posture of the industry.
- Log analysis and correlation: Security logs provide valuable insights into endpoint activities and security events. By analyzing and correlating logs from multiple endpoints, organizations can identify patterns and trends that may indicate potential threats. Log analysis tools can also be used to generate alerts and notifications, and to automate incident response procedures.
By gaining visibility into endpoint activities and security posture, organizations can significantly improve their ability to detect and respond to threats. Visibility enables organizations to identify potential threats early on, prioritize their response efforts, and take proactive steps to prevent and mitigate security incidents.
Automation
Automation plays a critical role in endpoint defense and response by streamlining security tasks and improving efficiency. Automated tools and processes can perform repetitive and time-consuming tasks, freeing up security analysts to focus on more strategic and complex activities. This can significantly improve the overall effectiveness and efficiency of endpoint security operations.
- Automated threat detection and response: Automated tools can monitor endpoints for suspicious activity and automatically respond to threats. This can help organizations to detect and respond to threats more quickly and effectively, reducing the risk of data breaches and other security incidents.
- Automated patching and vulnerability management: Automated tools can patch software vulnerabilities and update security configurations on endpoints. This can help organizations to keep their endpoints up-to-date and secure, reducing the risk of exploitation by attackers.
- Automated endpoint monitoring and reporting: Automated tools can monitor endpoint activity and generate reports on security events. This can help organizations to identify trends and patterns in endpoint activity, and to improve their overall security posture.
- Automated incident investigation and analysis: Automated tools can collect and analyze data from endpoints to investigate security incidents. This can help organizations to identify the root cause of security incidents and to develop more effective response strategies.
By automating endpoint security tasks, organizations can improve their overall security posture, reduce the risk of security breaches, and free up security analysts to focus on more strategic activities. Automation is an essential component of a comprehensive endpoint defense and response strategy.
Integration
Integration is a critical aspect of endpoint defense and response, as it enables organizations to connect endpoint security solutions with other security tools and platforms to achieve comprehensive threat protection. By integrating endpoint security solutions with other security tools, organizations can gain a more complete view of their security posture, improve threat detection and response capabilities, and automate security processes.
- Centralized visibility and management: Integration enables organizations to centralize visibility and management of endpoint security and other security tools. This provides a single pane of glass view of the security posture, allowing organizations to identify and respond to threats more quickly and effectively.
- Improved threat detection and response: Integration enables endpoint security solutions to share threat intelligence and event data with other security tools, such as security information and event management (SIEM) systems and threat intelligence platforms. This improves threat detection and response capabilities, as organizations can correlate events from multiple sources to identify and respond to threats more effectively.
- Automated security processes: Integration enables the automation of security processes, such as threat detection, investigation, and response. This can improve the efficiency and effectiveness of endpoint security operations, and free up security analysts to focus on more strategic tasks.
By integrating endpoint security solutions with other security tools and platforms, organizations can improve their overall security posture, reduce the risk of security breaches, and improve the efficiency and effectiveness of their endpoint security operations. Integration is an essential component of a comprehensive endpoint defense and response strategy.
FAQs on Endpoint Defense and Response
Endpoint defense and response (EDR) is a critical aspect of cybersecurity, protecting endpoints such as laptops, desktops, and mobile devices from cyber threats. Here are some frequently asked questions about EDR:
Question 1: What is the importance of endpoint defense and response?
EDR is crucial for protecting endpoints from sophisticated cyberattacks, reducing the risk of data breaches and financial losses. It provides real-time monitoring, threat detection, and automated response mechanisms to swiftly identify and mitigate security incidents.
Question 2: What are the key components of an effective EDR solution?
EDR solutions typically include antivirus and anti-malware protection, intrusion detection and prevention systems (IDS/IPS), endpoint detection and response (EDR) capabilities, threat intelligence, and automated response mechanisms.
Question 3: How does EDR differ from traditional antivirus software?
EDR goes beyond traditional antivirus software by providing continuous monitoring, threat detection and response, and automated remediation capabilities. It offers a more comprehensive and proactive approach to endpoint security.
Question 4: What are the benefits of integrating EDR with other security tools?
Integrating EDR with other security tools, such as SIEM and threat intelligence platforms, enhances threat detection and response capabilities. It provides a centralized view of security events, automates security processes, and improves overall security posture.
Question 5: How can organizations improve the effectiveness of their EDR strategy?
Organizations can enhance EDR effectiveness by implementing a layered security approach, regularly updating and patching software, conducting security audits, and providing ongoing security awareness training for employees.
Question 6: What are the emerging trends in EDR?
EDR is evolving with the use of artificial intelligence (AI) and machine learning (ML) for threat detection, automated response, and threat hunting. Cloud-based EDR solutions are also gaining popularity, offering scalability and cost-effectiveness.
In summary, endpoint defense and response is essential for safeguarding endpoints from cyber threats. EDR solutions provide comprehensive protection, threat detection, and automated response capabilities. By integrating EDR with other security tools and implementing best practices, organizations can significantly enhance their endpoint security posture and protect their valuable assets.
Transition to the next article section: Endpoint defense and response is a critical component of a comprehensive cybersecurity strategy. To further strengthen endpoint security, organizations should consider implementing additional measures such as network segmentation, data encryption, and regular security audits.
Endpoint Defense and Response Best Practices
To enhance the effectiveness of endpoint defense and response (EDR) strategies, organizations should consider implementing the following best practices:
Tip 1: Implement a Layered Security Approach
Deploy multiple layers of security controls, including EDR solutions, firewalls, intrusion detection systems, and anti-malware software, to create a comprehensive defense-in-depth strategy.
Tip 2: Regularly Update and Patch Software
Apply software updates and security patches promptly to address vulnerabilities and prevent attackers from exploiting them.
Tip 3: Conduct Regular Security Audits
Periodically assess the security posture of endpoints and networks to identify and address any weaknesses or misconfigurations.
Tip 4: Provide Security Awareness Training
Educate employees on cybersecurity best practices and the importance of recognizing and reporting suspicious activity.
Tip 5: Implement Network Segmentation
Divide the network into smaller segments to limit the spread of malware and other threats.
Tip 6: Encrypt Sensitive Data
Protect sensitive data at rest and in transit using encryption technologies to minimize the risk of data breaches.
Tip 7: Monitor User Activity and System Logs
Establish a system for monitoring user activity and system logs to detect and investigate suspicious behavior promptly.
Tip 8: Utilize Threat Intelligence
Subscribe to threat intelligence feeds and services to stay informed about the latest threats and attack techniques.
By implementing these best practices, organizations can significantly enhance their endpoint defense and response capabilities and protect their valuable assets from cyber threats.
Transition to the article’s conclusion: Endpoint defense and response is a critical component of a comprehensive cybersecurity strategy. By adopting these best practices, organizations can strengthen their security posture, reduce the risk of successful cyberattacks, and ensure business continuity in the face of evolving threats.
Conclusion
Endpoint defense and response (EDR) is a critical aspect of cybersecurity, protecting endpoints such as laptops, desktops, and mobile devices from cyber threats. EDR involves detecting, preventing, and responding to malicious activities targeting these endpoints. By implementing robust EDR measures, organizations can safeguard their valuable data and assets, reduce the risk of financial losses, and maintain business continuity.
EDR encompasses various dimensions, including prevention, detection, response, visibility, automation, and integration. Organizations should adopt a comprehensive approach, implementing multiple layers of security controls and best practices to enhance their endpoint security posture. This includes deploying EDR solutions, regularly updating and patching software, conducting security audits, providing security awareness training, and utilizing threat intelligence. By embracing these measures, organizations can significantly reduce the risk of successful cyberattacks and ensure a strong security posture in the face of evolving threats.
Youtube Video: