Threat detection technology refers to systems and tools that are designed to identify and respond to potential threats to an […]
Category: Security Cyber
Master the Art of Advanced Threat Protection: Your Cybersecurity Fortress
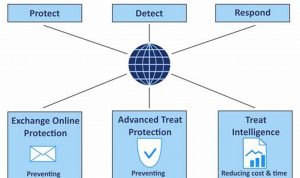
Advanced threat protection (ATP) is a comprehensive security solution that safeguards networks and systems from sophisticated and evolving cyber threats. […]
The Definitive Guide to Incident Detection and Response in Modern Cybersecurity
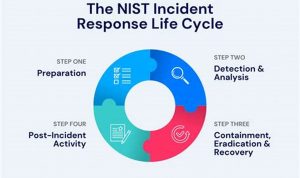
Incident detection and response is the process of identifying and responding to security incidents. It involves detecting suspicious activity, investigating […]
The Ultimate Guide to Data Protection for Enhanced Security
Data protection is a broad term that encompasses a wide range of practices designed to protect data from unauthorized access, […]
Master Security Information Management for Unstoppable Cyber Defense
Security information management (SIM) is the process of collecting, analyzing, and reporting on security-related information from multiple sources within an […]
Expert Endpoint Security Response for Enhanced Cyber Protection
Endpoint security response is a set of security measures designed to protect endpoints, which are devices such as laptops, desktops, […]
Uncover Hidden Breaches: Comprehensive Breach Detection Strategies
Breach detection is the process of identifying and responding to security breaches or attempted breaches. It involves monitoring network traffic, […]
Comprehensive Security Intelligence for Robust Cybersecurity
Security intelligence refers to the process of gathering and analyzing data to identify, prevent, and respond to security threats. It […]
Secure Your Endpoints: Comprehensive Endpoint Detection Platform for Cyber Threats
An endpoint detection platform (EPP) is a software solution that monitors and analyzes activities on endpoints (such as laptops, desktops, […]
Complete Endpoint Security Guide for Enhanced Cyber Protection
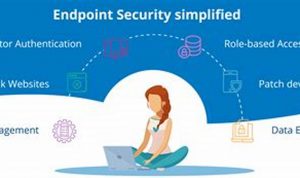
Endpoint security is a critical component of any organization’s cybersecurity strategy. It involves protecting devices such as laptops, desktops, smartphones, […]