Threat response tools empower organizations to proactively manage and mitigate potential risks and incidents. These tools provide real-time monitoring, threat […]
Category: Security Cyber
Automate Your Threat Response: Enhanced Security with Cutting-Edge Technology
Threat response automation is the use of technology to automate the detection, investigation, and response to cyber threats. This can […]
The Ultimate Guide to Host Protection: Safeguarding Your Servers from Cyber Threats
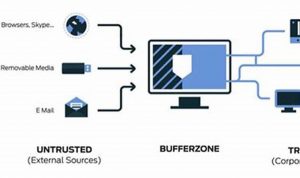
Host protection refers to the collective measures undertaken to safeguard a host environment from unauthorized access, malicious software, and other […]
Essential Endpoint Isolation: Protect Your Network from Threats
Endpoint isolation is a cybersecurity measure that involves isolating endpoints, such as laptops, desktops, and mobile devices, from the rest […]
Unparalleled Threat Detection Platform | Enhanced Cyber Security
Threat detection platform is a software solution that helps organizations to identify, analyze, and respond to potential threats to their […]
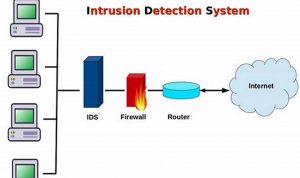
Secure Your Network with an Intrusion Detection System
An intrusion detection system (IDS) is a security mechanism used to detect unauthorized access to a computer system or network. […]
Early Warning System: Proactive Security Breach Detection for Enhanced Cybersecurity
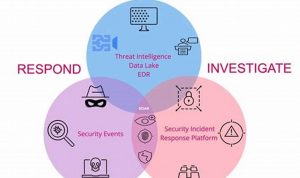
Security breach detection is the process of identifying and responding to security breaches or attempted breaches. These can include unauthorized […]
Mastering Security Incident Handling: A Comprehensive Guide to Protect Your Cybersecurity
Security incident handling, a critical aspect of cybersecurity, involves the strategies and procedures implemented by organizations to detect, analyze, and […]
Comprehensive Endpoint Threat Intelligence: Protect Your Devices
Endpoint threat intelligence gathers and analyzes data to provide comprehensive insights into potential threats and vulnerabilities at endpoints, which are […]
Latest Automated Response Innovations in Cybersecurity
Automated response refers to a pre-programmed or predetermined response generated by a computer system or software without human intervention. It […]