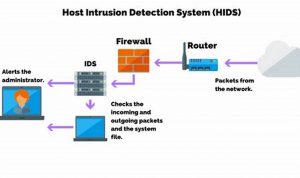
Endpoint threat monitoring is the practice of monitoring endpoints, such as laptops, desktops, and servers, for malicious activity. This can […]
Category: Security Cyber
The Ultimate Guide to Endpoint Visibility for Enhanced Cybersecurity
Endpoint visibility refers to the ability to monitor and manage endpoints, which are devices such as laptops, desktops, and smartphones […]
Master Host Detection and Response: Essential Security for Your Network
Host detection and response (HDR) is a crucial cybersecurity strategy that enables organizations to identify, contain, and remediate threats to […]
The Ultimate Guide to Cybersecurity Incident Response for Security Experts
Cybersecurity incident response is the process of responding to and recovering from a cybersecurity incident. It involves identifying the incident, […]
Ultimate Guide to Host-Based Security Systems for Enhanced Cybersecurity
A host-based security system is a type of security system that is installed on a computer or other device. It […]
Cyber Security's Guide to Advanced Detection and Response
Advanced detection and response is a security concept that involves using advanced technologies and techniques to detect and respond to […]
The Ultimate Guide to Threat Mitigation: Protecting Your Digital Assets from Cyber Attacks
Threat mitigation is the process of identifying, analyzing, and mitigating threats to an organization’s assets. It is a critical part […]
Ultimate Guide to Endpoint Breach Detection for Unstoppable Cybersecurity
Endpoint breach detection is a cybersecurity measure focused on identifying and responding to security breaches that target endpoints, the devices […]
All-Encompassing Endpoint Incident Response Strategies
Endpoint incident response is a critical aspect of modern cybersecurity. It refers to the strategies and actions taken to detect, […]
Essential Malware Prevention: Safeguard Your Systems from Cyber Threats
Malware prevention refers to the proactive measures taken to protect computer systems, networks, and devices from malicious software, known as […]