Revolutionize Cybersecurity with Automated Threat Detection
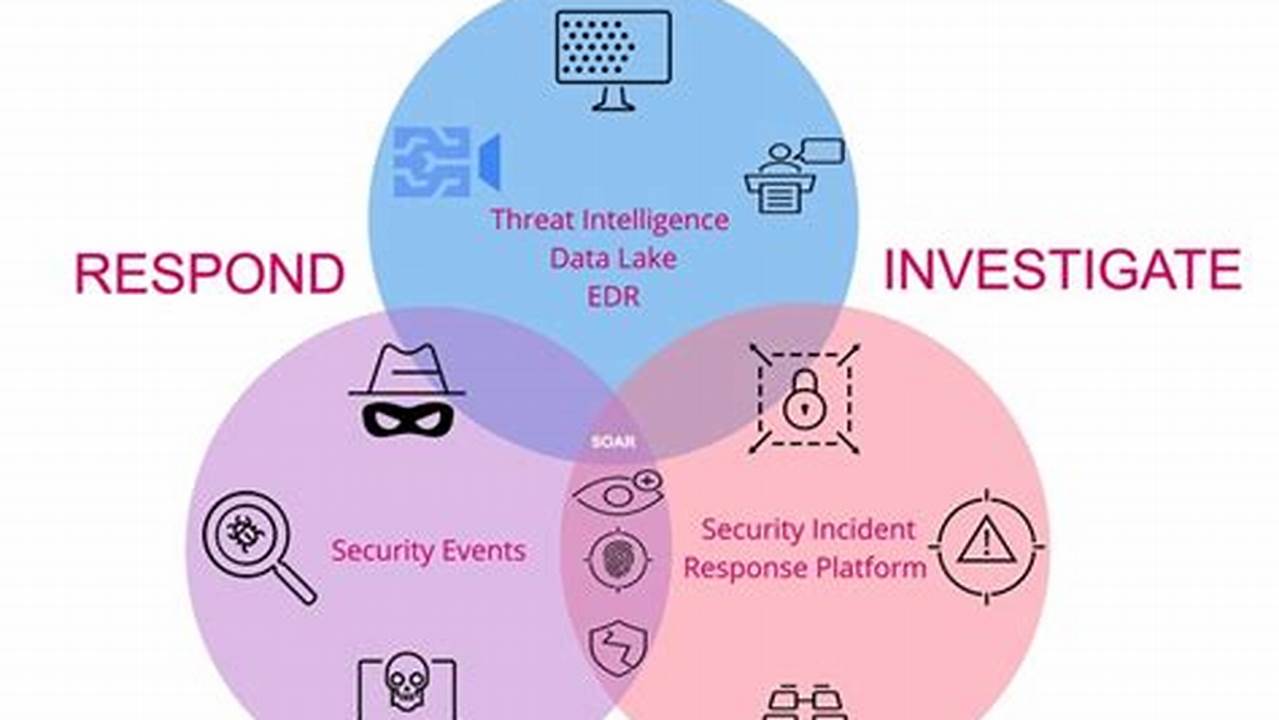
Automated threat detection is the process of using software tools to identify and respond to potential threats in a timely manner. These tools monitor network traffic, system logs, and other data sources for suspicious activity. When a potential threat is detected, the tool can take automated actions such as blocking the threat, quarantining infected files, or sending an alert to a security analyst.
Automated threat detection is an important part of a comprehensive security strategy. It can help organizations to detect and respond to threats more quickly and effectively, reducing the risk of a successful cyberattack. Automated threat detection tools can also help organizations to improve their compliance with regulatory requirements.
The use of automated threat detection tools has increased significantly in recent years as the number and sophistication of cyber threats has grown. Organizations of all sizes are now using these tools to protect their networks and data.
Automated threat detection
Automated threat detection is a critical aspect of cybersecurity, enabling organizations to proactively identify and respond to potential threats in a timely manner. Key aspects of automated threat detection include:
- Detection: Identifying potential threats through analysis of data sources.
- Response: Taking automated actions to mitigate threats, such as blocking or quarantining.
- Monitoring: Continuous surveillance of network traffic and system logs for suspicious activity.
- Analysis: Utilizing machine learning and other techniques to identify patterns and anomalies.
- Reporting: Providing alerts and reports on detected threats to security analysts.
- Integration: Seamlessly connecting with other security tools and systems for comprehensive protection.
These aspects work together to provide organizations with a robust and effective automated threat detection system. For instance, by continuously monitoring network traffic and analyzing system logs, automated threat detection tools can identify suspicious patterns and anomalies that may indicate a potential threat. The system can then automatically respond to the threat by blocking it, quarantining infected files, or sending an alert to a security analyst for further investigation.
Detection
Detection is a critical component of automated threat detection. Automated threat detection systems use a variety of techniques to identify potential threats, including:
- Signature-based detection: This technique compares incoming data to known threat signatures. If a match is found, the system identifies the data as malicious.
- Anomaly-based detection: This technique identifies data that deviates from normal patterns. Deviations from normal patterns may indicate a potential threat.
- Heuristic-based detection: This technique uses a set of rules to identify potential threats. These rules are based on the behavior of known threats.
- Machine learning-based detection: This technique uses machine learning algorithms to identify potential threats. These algorithms can learn from historical data to identify new and unknown threats.
By using a combination of these techniques, automated threat detection systems can identify a wide range of potential threats. This enables organizations to take action to mitigate these threats before they can cause damage.
Response
Response is a critical component of automated threat detection. Automated threat detection systems can identify potential threats, but they need to be able to take action to mitigate these threats. Automated threat detection systems can take a variety of automated actions, including:
- Blocking threats: Automated threat detection systems can block threats at the network level, preventing them from reaching their intended target.
- Quarantining threats: Automated threat detection systems can quarantine threats, preventing them from spreading to other systems.
- Deleting threats: Automated threat detection systems can delete threats, removing them from the system.
- Sending alerts: Automated threat detection systems can send alerts to security analysts, notifying them of potential threats.
The ability to take automated actions is essential for effective automated threat detection. Automated threat detection systems can identify potential threats quickly, but they need to be able to take action to mitigate these threats before they can cause damage.
Automated threat detection systems are used by organizations of all sizes to protect their networks and data. Automated threat detection systems can help organizations to detect and respond to threats more quickly and effectively, reducing the risk of a successful cyberattack.
Monitoring
Automated threat detection systems rely on continuous monitoring of network traffic and system logs to identify potential threats. This monitoring is essential for detecting threats in a timely manner, before they can cause damage.
- Network traffic monitoring: Automated threat detection systems monitor network traffic for suspicious activity, such as unusual patterns or attempts to access unauthorized resources.
- System log monitoring: Automated threat detection systems monitor system logs for suspicious activity, such as failed login attempts or changes to critical system files.
- Event correlation: Automated threat detection systems can correlate events from multiple sources, such as network traffic and system logs, to identify potential threats that would not be visible from any single source.
- Real-time analysis: Automated threat detection systems perform real-time analysis of monitored data to identify potential threats as quickly as possible.
By continuously monitoring network traffic and system logs, automated threat detection systems can identify potential threats in a timely manner, before they can cause damage. This monitoring is essential for effective automated threat detection.
Analysis
Analysis is a critical component of automated threat detection. Automated threat detection systems use a variety of techniques to analyze monitored data and identify potential threats, including:
- Machine learning: Machine learning algorithms can be trained to identify patterns and anomalies in data. This enables automated threat detection systems to identify potential threats that would not be visible to traditional signature-based or anomaly-based detection techniques.
- Statistical analysis: Statistical analysis can be used to identify deviations from normal patterns. This enables automated threat detection systems to identify potential threats that are not easily detectable using other techniques.
- Heuristic analysis: Heuristic analysis uses a set of rules to identify potential threats. These rules are based on the behavior of known threats.
By utilizing machine learning and other techniques to analyze monitored data, automated threat detection systems can identify a wide range of potential threats. This enables organizations to take action to mitigate these threats before they can cause damage.
Reporting
Reporting is an essential component of automated threat detection. Automated threat detection systems can identify potential threats, but they need to be able to communicate these threats to security analysts in a clear and concise manner. Reporting can take a variety of forms, including alerts, reports, and dashboards.
- Alerts: Alerts are real-time notifications that are sent to security analysts when a potential threat is detected. Alerts typically include information about the threat, such as the source of the threat, the target of the threat, and the severity of the threat.
- Reports: Reports are detailed summaries of detected threats. Reports typically include information about the threat, such as the date and time of the threat, the source of the threat, the target of the threat, the severity of the threat, and the actions that were taken to mitigate the threat.
- Dashboards: Dashboards are graphical representations of detected threats. Dashboards typically provide a high-level overview of the threats that have been detected, as well as the status of these threats.
Reporting is essential for effective automated threat detection. Reporting enables security analysts to quickly and easily identify and respond to potential threats. Reporting also provides security analysts with valuable information that can be used to improve the effectiveness of automated threat detection systems.
Integration
Integration is essential for effective automated threat detection. Automated threat detection systems can identify potential threats, but they need to be able to communicate with other security tools and systems in order to take action to mitigate these threats. Integration enables automated threat detection systems to share information with other security tools and systems, such as firewalls, intrusion detection systems, and security information and event management (SIEM) systems. This enables organizations to create a comprehensive security strategy that can detect, prevent, and respond to threats in a coordinated manner.
- Centralized management: Integration enables organizations to manage all of their security tools and systems from a single console. This makes it easier to configure and maintain security systems, and it also provides a single pane of glass for monitoring security events.
- Automated response: Integration enables automated threat detection systems to automatically take action to mitigate threats. For example, an automated threat detection system could automatically block a malicious IP address or quarantine a malicious file.
- Improved threat intelligence: Integration enables automated threat detection systems to share threat intelligence with other security tools and systems. This enables organizations to build a more comprehensive picture of the threat landscape, and it also helps to ensure that all security tools and systems are using the most up-to-date threat intelligence.
- Enhanced compliance: Integration can help organizations to comply with regulatory requirements. Many regulations require organizations to have a comprehensive security strategy that includes automated threat detection. Integration makes it easier to meet these requirements by providing a single, centralized view of security events.
Integration is an essential part of any effective automated threat detection strategy. Integration enables organizations to create a comprehensive security strategy that can detect, prevent, and respond to threats in a coordinated manner.
Automated Threat Detection FAQs
This section addresses frequently asked questions about automated threat detection to provide a comprehensive understanding of its significance and functionalities.
Question 1: What is automated threat detection?
Answer: Automated threat detection is the process of using software tools to identify and respond to potential threats in a timely manner. These tools monitor network traffic, system logs, and other data sources for suspicious activity. When a potential threat is detected, the tool can take automated actions such as blocking the threat, quarantining infected files, or sending an alert to a security analyst.
Question 2: Why is automated threat detection important?
Answer: Automated threat detection is important because it can help organizations to detect and respond to threats more quickly and effectively, reducing the risk of a successful cyberattack. Automated threat detection tools can also help organizations to improve their compliance with regulatory requirements.
Question 3: What are the benefits of using automated threat detection tools?
Answer: The benefits of using automated threat detection tools include improved threat detection and response times, reduced risk of successful cyberattacks, improved compliance with regulatory requirements, and reduced workload for security analysts.
Question 4: What are the different types of automated threat detection techniques?
Answer: The different types of automated threat detection techniques include signature-based detection, anomaly-based detection, heuristic-based detection, and machine learning-based detection.
Question 5: How can organizations implement automated threat detection?
Answer: Organizations can implement automated threat detection by purchasing and deploying automated threat detection software tools. These tools can be deployed on-premises or in the cloud.
Question 6: What are the challenges of using automated threat detection tools?
Answer: The challenges of using automated threat detection tools include the cost of the tools, the complexity of the tools, and the need for skilled security analysts to manage the tools.
Summary: Automated threat detection is a critical component of a comprehensive cybersecurity strategy. It can help organizations to detect and respond to threats more quickly and effectively, reducing the risk of a successful cyberattack.
Transition: To delve deeper into the technical aspects of automated threat detection, refer to the main article for a detailed exploration.
Automated Threat Detection Tips
Implementing automated threat detection can significantly enhance an organization’s cybersecurity posture. Here are some essential tips to consider:
Tip 1: Choose a comprehensive solution: Opt for an automated threat detection tool that offers a comprehensive range of features, including network traffic monitoring, system log analysis, and endpoint protection.
Tip 2: Prioritize threat intelligence: Integrate threat intelligence feeds into your automated threat detection system to stay informed about the latest threats and vulnerabilities.
Tip 3: Leverage machine learning: Utilize machine learning algorithms to enhance threat detection capabilities. Machine learning can identify patterns and anomalies that may be missed by traditional methods.
Tip 4: Automate response actions: Configure automated threat detection tools to take immediate actions upon threat detection, such as blocking malicious traffic or quarantining infected files.
Tip 5: Integrate with other security tools: Ensure your automated threat detection solution integrates seamlessly with other security tools, such as firewalls and intrusion detection systems, for a holistic defense strategy.
Tip 6: Regularly review and tune: Continuously review and refine the configuration of your automated threat detection system to optimize its effectiveness and minimize false positives.
Tip 7: Train your team: Provide regular training to your security team on the operation and maintenance of your automated threat detection system to ensure its efficient utilization.
Tip 8: Stay updated with industry best practices: Keep abreast of the latest industry best practices and advancements in automated threat detection to maintain a robust security posture.
Summary: Implementing these tips can help organizations leverage automated threat detection to strengthen their cybersecurity defenses, proactively detect and respond to threats, and minimize the risk of successful cyberattacks.
Transition: Explore the comprehensive article for in-depth insights into automated threat detection strategies and their significance in today’s evolving threat landscape.
Conclusion
Automated threat detection is a critical component of a comprehensive cybersecurity strategy. It enables organizations to detect and respond to threats more quickly and effectively, reducing the risk of a successful cyberattack. Automated threat detection tools use a variety of techniques to identify potential threats, including signature-based detection, anomaly-based detection, heuristic-based detection, and machine learning-based detection.
Organizations can implement automated threat detection by purchasing and deploying automated threat detection software tools. These tools can be deployed on-premises or in the cloud. The cost of automated threat detection tools varies depending on the features and capabilities of the tool. Organizations should carefully evaluate their needs and budget before selecting an automated threat detection tool.
Automated threat detection is an essential part of any effective cybersecurity strategy. It can help organizations to protect their networks and data from a wide range of threats.
Youtube Video:
