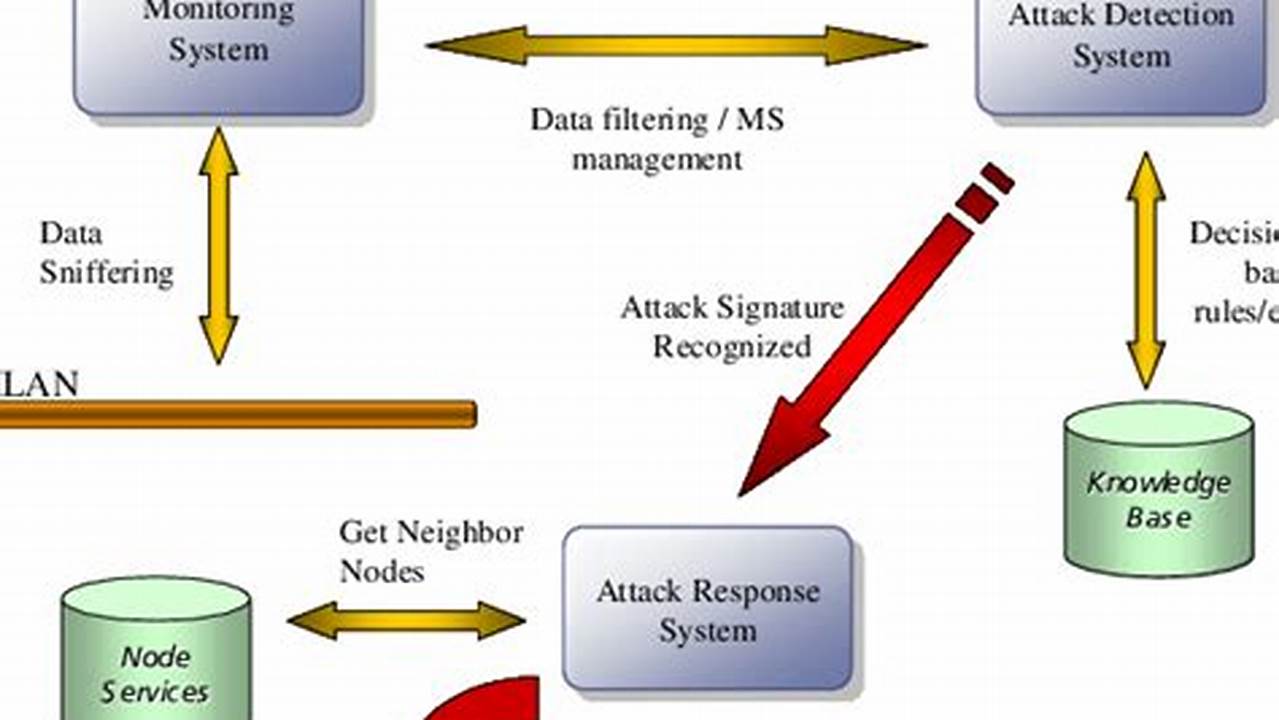
An attack detection system (ADS) monitors a computer system or network for malicious activity or policy violations. It can detect a wide range of attacks, including those that target the network, the operating system, or specific applications. ADSs use a variety of techniques to detect attacks, including signature-based detection, anomaly-based detection, and heuristic-based detection.
ADSs are an important part of a comprehensive security strategy. They can help to protect systems from a variety of threats, and they can also provide valuable information about the nature of attacks. This information can be used to improve security defenses and to develop new countermeasures.
The first ADSs were developed in the 1980s. Since then, ADSs have become increasingly sophisticated, and they are now used in a wide range of applications. ADSs are used to protect everything from small businesses to large enterprises. They are also used to protect critical infrastructure, such as power plants and financial institutions.
Attack detection system
An attack detection system (ADS) is a critical component of any cybersecurity strategy. ADSs monitor network traffic and system activity for suspicious activity that may indicate an attack. When an ADS detects an attack, it can take a variety of actions, such as alerting security personnel, blocking the attack, or quarantining infected systems.
- Detection methods: ADSs use a variety of techniques to detect attacks, including signature-based detection, anomaly-based detection, and heuristic-based detection.
- Types of attacks: ADSs can detect a wide range of attacks, including network attacks, host-based attacks, and application attacks.
- Deployment options: ADSs can be deployed on-premises or in the cloud.
- Benefits: ADSs provide a number of benefits, including improved security, reduced risk of data breaches, and compliance with regulations.
- Challenges: ADSs can be complex to manage and maintain, and they can generate a large number of false positives.
Overall, ADSs are an essential part of any cybersecurity strategy. They can help organizations to detect and respond to attacks quickly and effectively, reducing the risk of data breaches and other security incidents.
Detection methods
Attack detection systems (ADSs) rely on a variety of detection methods to identify malicious activity. These methods can be broadly categorized into three main types: signature-based detection, anomaly-based detection, and heuristic-based detection.
Signature-based detection is the most common type of attack detection method. It involves comparing network traffic or system activity to a database of known attack signatures. If a match is found, the ADS will generate an alert.
Anomaly-based detection is a more sophisticated type of attack detection method. It involves monitoring network traffic or system activity for unusual or unexpected behavior. If an anomaly is detected, the ADS will generate an alert.
Heuristic-based detection is a type of attack detection method that uses a set of rules or heuristics to identify malicious activity. These heuristics are typically based on the behavior of known attacks.
The choice of detection method depends on a number of factors, including the type of attack being detected, the performance requirements of the ADS, and the cost of the ADS. Signature-based detection is typically the most effective method for detecting known attacks. However, it can be less effective at detecting new or unknown attacks.
Anomaly-based detection is more effective at detecting new or unknown attacks. However, it can be more difficult to configure and maintain than signature-based detection.
Heuristic-based detection is a compromise between signature-based detection and anomaly-based detection. It can be effective at detecting both known and unknown attacks. However, it can be more difficult to develop and maintain than signature-based detection or anomaly-based detection.
By using a variety of detection methods, ADSs can provide a high level of protection against a wide range of attacks.
Types of attacks
Attack detection systems (ADSs) are designed to detect a wide range of attacks, including network attacks, host-based attacks, and application attacks. This is important because different types of attacks require different detection methods.
Network attacks target the network infrastructure, such as routers and switches. These attacks can disrupt network traffic and prevent users from accessing resources. ADSs can detect network attacks by monitoring network traffic for suspicious activity, such as ungewhnliche Paketgren oder Datenverkehrsmuster.
Host-based attacks target individual hosts, such as servers and workstations. These attacks can compromise the host’s operating system, applications, or data. ADSs can detect host-based attacks by monitoring system activity for suspicious activity, such as ungewhnliche Prozesse oder Dateizugriffe.
Application attacks target specific applications, such as web browsers and email clients. These attacks can exploit vulnerabilities in the application to gain unauthorized access to the user’s system. ADSs can detect application attacks by monitoring application activity for suspicious activity, such as ungewhnliche Eingaben oder Ausgaben.
By detecting a wide range of attacks, ADSs can help organizations to protect their networks and systems from a variety of threats. This can help to reduce the risk of data breaches, financial losses, and reputational damage.
Deployment options
The deployment option for an attack detection system (ADS) is a critical decision that can impact the overall security posture of an organization. ADSs can be deployed on-premises or in the cloud, and each option has its own advantages and disadvantages.
-
On-premises deployment
With on-premises deployment, the ADS is installed and managed on the organization’s own hardware and network. This gives the organization complete control over the ADS and its data. However, on-premises deployment can be more expensive and complex to manage than cloud deployment. -
Cloud deployment
With cloud deployment, the ADS is hosted by a third-party provider. This can be more cost-effective and easier to manage than on-premises deployment. However, cloud deployment may not be suitable for organizations with sensitive data or strict compliance requirements.
The decision of whether to deploy an ADS on-premises or in the cloud should be based on a number of factors, including the organization’s security requirements, budget, and IT resources. Organizations should carefully consider the pros and cons of each option before making a decision.
Benefits
Attack detection systems (ADSs) provide a number of benefits to organizations, including improved security, reduced risk of data breaches, and compliance with regulations.
Improved security: ADSs can help organizations to improve their security posture by detecting and responding to attacks in real time. This can help to prevent data breaches, financial losses, and reputational damage.
Reduced risk of data breaches: ADSs can help organizations to reduce their risk of data breaches by detecting and blocking malicious activity. This can help to protect sensitive data from being accessed by unauthorized users.
Compliance with regulations: ADSs can help organizations to comply with a variety of regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA). These regulations require organizations to implement security measures to protect sensitive data.
In addition to these benefits, ADSs can also provide organizations with valuable insights into the nature of attacks. This information can be used to improve security defenses and to develop new countermeasures.
Overall, ADSs are an essential part of any cybersecurity strategy. They can help organizations to improve their security posture, reduce their risk of data breaches, and comply with regulations.
Challenges
Attack detection systems (ADSs) are complex systems that can be difficult to manage and maintain. This is due to the fact that ADSs must be constantly updated with the latest threat intelligence in order to be effective. In addition, ADSs can generate a large number of false positives, which can be time-consuming to investigate.
The challenges of managing and maintaining ADSs can be compounded by the fact that they are often deployed in large and complex networks. This can make it difficult to ensure that the ADS is properly configured and tuned to meet the specific needs of the network. As a result, ADSs can sometimes be ineffective at detecting attacks or may generate a large number of false positives.
Despite the challenges, ADSs are an essential part of any cybersecurity strategy. By detecting and responding to attacks in real time, ADSs can help to prevent data breaches, financial losses, and reputational damage.
Organizations should carefully consider the challenges of managing and maintaining ADSs before deploying them. Organizations should also ensure that they have the resources and expertise to properly manage and maintain their ADSs.
Attack Detection System FAQs
Attack detection systems (ADSs) are an essential part of any cybersecurity strategy. They can help organizations to detect and respond to attacks in real time, reducing the risk of data breaches, financial losses, and reputational damage.
Question 1: What are the different types of attack detection systems?
There are three main types of attack detection systems: signature-based, anomaly-based, and heuristic-based. Signature-based detection systems identify attacks by matching network traffic or system activity to a database of known attack signatures. Anomaly-based detection systems identify attacks by monitoring network traffic or system activity for unusual or unexpected behavior. Heuristic-based detection systems identify attacks by using a set of rules or heuristics to identify malicious activity.
Question 2: What are the benefits of using an attack detection system?
Attack detection systems provide a number of benefits, including improved security, reduced risk of data breaches, and compliance with regulations. ADSs can help organizations to improve their security posture by detecting and responding to attacks in real time. This can help to prevent data breaches, financial losses, and reputational damage.
Question 3: What are the challenges of using an attack detection system?
Attack detection systems can be complex to manage and maintain. They can also generate a large number of false positives, which can be time-consuming to investigate. In addition, ADSs can be expensive to deploy and maintain.
Question 4: How can I choose the right attack detection system for my organization?
When choosing an attack detection system, organizations should consider a number of factors, including the size and complexity of their network, the types of attacks they are most likely to face, and their budget. Organizations should also ensure that they have the resources and expertise to properly manage and maintain their ADS.
Question 5: What are some best practices for using an attack detection system?
Organizations should follow a number of best practices when using an attack detection system, including:
- Keep the ADS up to date with the latest threat intelligence.
- Tune the ADS to minimize false positives.
- Monitor the ADS for alerts and respond to them promptly.
- Use the ADS to improve security defenses and develop new countermeasures.
Question 6: What is the future of attack detection systems?
Attack detection systems are constantly evolving to keep pace with the changing threat landscape. In the future, we can expect to see ADSs that are more intelligent, automated, and integrated with other security technologies.
Summary of key takeaways or final thought
Attack detection systems are an essential part of any cybersecurity strategy. They can help organizations to detect and respond to attacks in real time, reducing the risk of data breaches, financial losses, and reputational damage. Organizations should carefully consider their needs and resources when choosing and deploying an ADS.
Transition to the next article section
…
Attack Detection System Tips
Attack detection systems (ADSs) are an essential part of any cybersecurity strategy. They can help organizations to detect and respond to attacks in real time, reducing the risk of data breaches, financial losses, and reputational damage. Here are five tips for using ADSs effectively:
Tip 1: Keep the ADS up to date with the latest threat intelligence.
Threat intelligence is information about the latest threats and vulnerabilities. By keeping the ADS up to date with the latest threat intelligence, organizations can ensure that the ADS is able to detect the latest attacks.
Tip 2: Tune the ADS to minimize false positives.
False positives are alerts that are generated by the ADS when there is no actual attack. False positives can be a nuisance and can waste time and resources. By tuning the ADS to minimize false positives, organizations can improve the accuracy of the ADS.
Tip 3: Monitor the ADS for alerts and respond to them promptly.
When the ADS generates an alert, it is important to investigate the alert promptly. By responding to alerts promptly, organizations can minimize the impact of attacks.
Tip 4: Use the ADS to improve security defenses and develop new countermeasures.
The ADS can provide valuable insights into the nature of attacks. This information can be used to improve security defenses and develop new countermeasures.
Tip 5: Regularly review and update your ADS strategy.
The threat landscape is constantly changing. As a result, it is important to regularly review and update your ADS strategy to ensure that it is still effective.
Summary of key takeaways or benefits
By following these tips, organizations can improve the effectiveness of their ADSs and reduce the risk of data breaches, financial losses, and reputational damage.
Transition to the article’s conclusion
…
Conclusion
Attack detection systems (ADSs) are an essential part of any cybersecurity strategy. They can help organizations to detect and respond to attacks in real time, reducing the risk of data breaches, financial losses, and reputational damage.
In this article, we have explored the different types of ADSs, the benefits of using ADSs, and the challenges of using ADSs. We have also provided some tips for using ADSs effectively.
As the threat landscape continues to evolve, it is important for organizations to invest in robust ADSs. ADSs can help organizations to protect their networks and data from a variety of threats.
Youtube Video: