Essential Threat Response Strategies for Enhanced Cyber Security
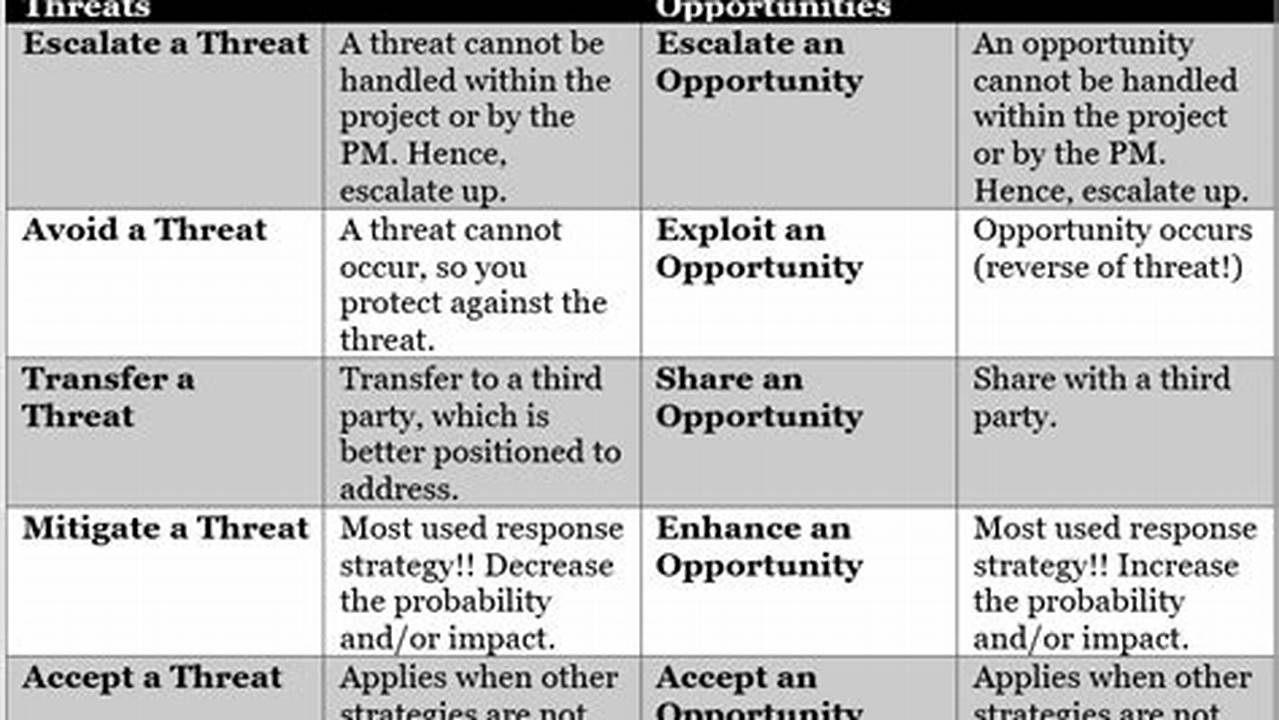
Every organization faces unique threats and challenges that can impact its operations, reputation, and financial stability. Threat response strategies are a set of proactive and reactive measures designed to identify, assess, and mitigate potential threats to an organization. These strategies are crucial for ensuring business continuity and minimizing the impact of security incidents, data breaches, natural disasters, or other disruptive events.
Effective threat response strategies involve a comprehensive approach that encompasses risk assessment, vulnerability management, incident response planning, and business continuity planning. By proactively identifying potential threats and implementing appropriate safeguards, organizations can reduce the likelihood of security breaches and minimize the impact of successful attacks. Threat response strategies also provide a framework for responding to incidents in a timely and coordinated manner, ensuring that the organization can quickly recover and resume normal operations.
…
Threat response strategies
Threat response strategies are essential for protecting organizations from a wide range of threats, including cyberattacks, data breaches, natural disasters, and other disruptive events. These strategies involve a comprehensive approach that encompasses:
- Identification: Identifying potential threats and vulnerabilities
- Assessment: Evaluating the likelihood and impact of threats
- Mitigation: Implementing safeguards to reduce the risk of threats
- Response: Developing plans for responding to and recovering from incidents
- Communication: Establishing clear communication channels for sharing information about threats and incidents
- Training: Educating employees on their role in threat response
- Testing: Regularly testing threat response plans to ensure their effectiveness
- Review: Continuously reviewing and updating threat response strategies based on changing conditions
By focusing on these key aspects, organizations can develop and implement effective threat response strategies that will help them to protect their assets, reputation, and operations.
Identification
Identifying potential threats and vulnerabilities is the foundation of effective threat response strategies. By understanding the threats that an organization faces, and the vulnerabilities that could be exploited, organizations can take steps to mitigate risks and prevent incidents from occurring. For example, an organization that identifies a vulnerability in its IT systems could implement a patch or upgrade to fix the vulnerability, reducing the risk of a cyberattack.
Threat identification and vulnerability assessment are ongoing processes. As new threats emerge and vulnerabilities are discovered, organizations must continuously review and update their threat response strategies. This requires collaboration between IT security, risk management, and business units to ensure that all potential threats are considered and appropriate safeguards are in place.
The benefits of effective threat identification and vulnerability assessment include:
- Reduced risk of security breaches and data breaches
- Improved compliance with regulatory requirements
- Enhanced business continuity and resilience
- Reduced costs associated with incident response and recovery
Organizations that fail to adequately identify and assess threats and vulnerabilities are at increased risk of security incidents and data breaches. By investing in effective threat response strategies, organizations can protect their assets, reputation, and operations.
Assessment
Evaluating the likelihood and impact of threats is a critical component of threat response strategies. By understanding the likelihood of a threat occurring and the potential impact it could have on the organization, organizations can prioritize their resources and develop appropriate mitigation strategies.
- Likelihood assessment involves examining factors such as the threat actor’s capabilities, motivation, and past behavior, as well as the organization’s vulnerabilities and security controls. For example, an organization that operates in a high-risk industry may be more likely to be targeted by cyberattacks, while an organization with strong security controls may be less likely to experience a data breach.
- Impact assessment involves evaluating the potential consequences of a threat occurring, such as financial losses, reputational damage, or operational disruptions. For example, a cyberattack that disrupts the organization’s IT systems could lead to lost revenue, data loss, and reputational damage.
By combining likelihood and impact assessments, organizations can develop a threat risk assessment matrix that helps them to prioritize threats and allocate resources accordingly. This matrix can be used to develop and implement threat response strategies that are tailored to the specific threats that the organization faces.
Effective threat assessment requires ongoing monitoring and analysis of the threat landscape. As new threats emerge and existing threats evolve, organizations must continuously review and update their threat assessments. This ensures that the organization is always prepared to respond to the latest threats and minimize their impact.
Mitigation
Mitigation is a critical component of threat response strategies, as it involves implementing safeguards to reduce the risk of threats occurring. By taking steps to mitigate threats, organizations can reduce the likelihood of a security incident or data breach, and minimize the impact if one does occur.
There are a variety of mitigation strategies that organizations can implement, depending on the specific threats they face. These strategies can include:
- Implementing technical safeguards, such as firewalls, intrusion detection systems, and antivirus software
- Implementing physical safeguards, such as access control systems and security cameras
- Implementing administrative safeguards, such as security policies and procedures
- Educating employees on security best practices
- Developing and implementing incident response plans
Organizations should prioritize mitigation strategies based on the likelihood and impact of the threats they face. For example, an organization that faces a high risk of cyberattacks may prioritize implementing technical safeguards, such as firewalls and intrusion detection systems. An organization that faces a high risk of data breaches may prioritize educating employees on security best practices and developing an incident response plan.
Effective mitigation strategies require ongoing monitoring and review. As new threats emerge and existing threats evolve, organizations must continuously review and update their mitigation strategies. This ensures that the organization is always prepared to respond to the latest threats and minimize their impact.
Response
Response is a critical component of threat response strategies, as it involves developing plans for responding to and recovering from incidents. By having a plan in place, organizations can minimize the impact of an incident and restore normal operations as quickly as possible.
- Incident response planning involves identifying potential incidents, developing procedures for responding to those incidents, and assigning responsibilities to key personnel. For example, an organization may develop an incident response plan for a cyberattack that includes steps for isolating the affected systems, notifying law enforcement, and communicating with customers.
- Business continuity planning involves developing plans for recovering from an incident and restoring normal operations. For example, an organization may develop a business continuity plan for a natural disaster that includes steps for evacuating employees, relocating to a backup site, and resuming critical operations.
- Testing and training are essential for ensuring that incident response and business continuity plans are effective. Organizations should regularly test their plans and train employees on their roles and responsibilities. This ensures that everyone knows what to do in the event of an incident.
- Communication is also critical during an incident. Organizations should develop a communication plan that outlines how they will communicate with employees, customers, and other stakeholders during and after an incident.
Effective incident response and business continuity planning can help organizations to minimize the impact of an incident and restore normal operations as quickly as possible. By having a plan in place, organizations can reduce the risk of financial losses, reputational damage, and operational disruptions.
Communication
Communication is a critical component of threat response strategies, as it ensures that all stakeholders are aware of potential and current threats and incidents, and that they have the information they need to respond appropriately. Clear communication channels allow organizations to share information quickly and efficiently, which can help to minimize the impact of an incident and restore normal operations as quickly as possible.
- Incident notification: Organizations should establish clear procedures for notifying stakeholders of security incidents. This includes identifying who should be notified, how they should be notified, and what information should be included in the notification.
- Information sharing: Organizations should establish processes for sharing information about threats and incidents with other organizations and government agencies. This can help to improve the overall security posture of the industry and reduce the risk of future incidents.
- Employee communication: Organizations should communicate with employees about security threats and incidents in a clear and concise manner. This helps to ensure that employees are aware of the risks and that they know what to do in the event of an incident.
- Customer communication: Organizations should communicate with customers about security incidents that may impact them. This helps to maintain customer trust and confidence, and it can also help to mitigate the reputational damage that can result from a security incident.
Effective communication is essential for effective threat response strategies. By establishing clear communication channels and processes, organizations can ensure that all stakeholders are aware of potential and current threats and incidents, and that they have the information they need to respond appropriately.
Training
Educating employees on their role in threat response is a critical component of effective threat response strategies. Employees are often the first line of defense against security threats, and their actions can have a significant impact on the organization’s ability to prevent, detect, and respond to incidents.
-
Identifying and reporting threats
Employees need to be trained to identify potential threats, such as phishing emails, suspicious activity on the network, or unauthorized access to physical assets. They also need to know how to report these threats to the appropriate authorities within the organization. -
Responding to incidents
Employees need to be trained on how to respond to security incidents, such as data breaches, ransomware attacks, or physical security breaches. This training should include procedures for isolating the affected systems, notifying the appropriate authorities, and preserving evidence. -
Protecting sensitive data
Employees need to be trained on how to protect sensitive data, such as customer information, financial data, and intellectual property. This training should include best practices for data handling, storage, and disposal. -
Maintaining security awareness
Employees need to be trained on the importance of maintaining security awareness and vigilance. This training should include information on the latest security threats and trends, as well as tips for staying safe online and offline.
By providing employees with the training and education they need, organizations can empower them to play a vital role in protecting the organization from security threats. This training can help to reduce the risk of security incidents, minimize the impact of incidents that do occur, and ensure that the organization is better prepared to respond to and recover from security breaches.
Testing
Testing threat response plans is a critical component of effective threat response strategies. Regularly testing these plans ensures that they are up-to-date, effective, and will work as intended in the event of a real-world incident. Without regular testing, organizations cannot be confident that their threat response plans will be effective when they are needed most.
There are a number of different ways to test threat response plans. One common method is to conduct tabletop exercises, which simulate a real-world incident and allow participants to test their response procedures. Another method is to conduct penetration testing, which involves hiring a third-party security firm to attempt to breach an organization’s security defenses. Penetration testing can help to identify vulnerabilities in an organization’s security posture and provide valuable feedback on the effectiveness of the organization’s threat response plans.
Regardless of the method used, it is important to test threat response plans on a regular basis. This will help to ensure that the plans are up-to-date and effective, and that all stakeholders are familiar with their roles and responsibilities in the event of an incident.
Review
The threat landscape is constantly evolving, with new threats emerging all the time. To stay ahead of these threats, organizations need to continuously review and update their threat response strategies. This involves:
-
Monitoring the threat landscape
Organizations need to stay up-to-date on the latest threats and trends. This can be done by reading security blogs and articles, attending security conferences, and talking to other security professionals. -
Assessing the organization’s risk
Once the organization is aware of the latest threats, it needs to assess its risk of being attacked. This involves identifying the organization’s vulnerabilities and determining the likelihood and impact of an attack. -
Updating threat response plans
Based on the organization’s risk assessment, it needs to update its threat response plans. These plans should outline the steps that the organization will take to prevent, detect, and respond to an attack. -
Testing threat response plans
Once the organization’s threat response plans have been updated, they need to be tested to ensure that they are effective. This can be done by conducting tabletop exercises or penetration tests.
By continuously reviewing and updating their threat response strategies, organizations can stay ahead of the latest threats and protect themselves from attack.
Threat Response Strategies FAQs
Threat response strategies are critical for organizations of all sizes to protect themselves from a wide range of threats, including cyberattacks, data breaches, natural disasters, and other disruptive events. These strategies involve a comprehensive approach that encompasses risk assessment, vulnerability management, incident response planning, and business continuity planning.
Question 1: Why are threat response strategies important?
Threat response strategies are important because they help organizations to:
- Identify and assess potential threats
- Develop plans to prevent and mitigate threats
- Respond to and recover from incidents
- Minimize the impact of threats and protect the organization’s assets, reputation, and operations
Question 2: What are the key components of a threat response strategy?
The key components of a threat response strategy include:
- Risk assessment: Identifying and assessing the potential threats that an organization faces
- Vulnerability management: Identifying and mitigating vulnerabilities that could be exploited by threats
- Incident response planning: Developing plans for responding to and recovering from incidents
- Business continuity planning: Developing plans for continuing operations in the event of a disruptive event
Question 3: How can organizations develop effective threat response strategies?
Organizations can develop effective threat response strategies by:
- Understanding the threats that they face
- Assessing their vulnerabilities
- Developing plans to prevent and mitigate threats
- Testing their plans and training employees on their roles and responsibilities
- Regularly reviewing and updating their strategies
Question 4: What are some common challenges in implementing threat response strategies?
Some common challenges in implementing threat response strategies include:
- Lack of resources
- Lack of expertise
- Lack of coordination between different departments
- Changing threat landscape
Question 5: What are the benefits of implementing threat response strategies?
The benefits of implementing threat response strategies include:
- Reduced risk of security breaches and data breaches
- Improved compliance with regulatory requirements
- Enhanced business continuity and resilience
- Reduced costs associated with incident response and recovery
Question 6: How can organizations improve the effectiveness of their threat response strategies?
Organizations can improve the effectiveness of their threat response strategies by:
- Regularly testing and updating their plans
- Training employees on their roles and responsibilities
- Conducting tabletop exercises and simulations
- Sharing information with other organizations and government agencies
- Staying up-to-date on the latest threats and trends
Threat response strategies are an essential part of protecting organizations from a wide range of threats. By understanding the threats that they face, assessing their vulnerabilities, and developing and implementing effective threat response strategies, organizations can reduce the risk of incidents and minimize the impact of those that do occur.
…
Threat Response Strategies Tips
Organizations can take a number of steps to improve the effectiveness of their threat response strategies, including:
Tip 1: Regularly test and update your plans
Threat response plans should be tested regularly to ensure that they are up-to-date and effective. This can be done through tabletop exercises or penetration tests.Tip 2: Train employees on their roles and responsibilities
All employees should be trained on their roles and responsibilities in the event of a security incident. This training should include information on how to identify and report threats, how to respond to incidents, and how to protect sensitive data.Tip 3: Conduct tabletop exercises and simulations
Tabletop exercises and simulations are a great way to test threat response plans and train employees on their roles and responsibilities. These exercises can be customized to simulate a variety of different scenarios, and they can help to identify areas for improvement in the organization’s threat response strategy.Tip 4: Share information with other organizations and government agencies
Organizations should share information about threats and incidents with other organizations and government agencies. This can help to improve the overall security posture of the industry and reduce the risk of future incidents.Tip 5: Stay up-to-date on the latest threats and trends
The threat landscape is constantly evolving, so it is important for organizations to stay up-to-date on the latest threats and trends. This can be done by reading security blogs and articles, attending security conferences, and talking to other security professionals.Tip 6: Implement a threat intelligence program
A threat intelligence program can help organizations to identify and track threats that are relevant to their business. This information can be used to improve the organization’s threat response strategy and to make better decisions about security investments.Tip 7: Use security automation tools
Security automation tools can help organizations to automate many of the tasks involved in threat response, such as threat detection, incident response, and security monitoring. This can free up security staff to focus on more strategic tasks.Tip 8: Develop a business continuity plan
A business continuity plan outlines the steps that an organization will take to continue operations in the event of a disruptive event, such as a natural disaster or a cyberattack. This plan should be reviewed and updated regularly to ensure that it is effective.By following these tips, organizations can improve the effectiveness of their threat response strategies and better protect themselves from a wide range of threats.
…
Conclusion
Threat response strategies are essential for organizations of all sizes to protect themselves from a wide range of threats, including cyberattacks, data breaches, natural disasters, and other disruptive events. These strategies involve a comprehensive approach that encompasses risk assessment, vulnerability management, incident response planning, and business continuity planning.
By understanding the threats that they face, assessing their vulnerabilities, and developing and implementing effective threat response strategies, organizations can reduce the risk of incidents and minimize the impact of those that do occur. This is an ongoing process that requires regular testing, updating, and training to ensure that the organization is always prepared to respond to the latest threats.
Threat response strategies are a critical part of protecting organizations from a wide range of threats. By taking the steps outlined in this article, organizations can improve the effectiveness of their threat response strategies and better protect themselves from a wide range of threats.
Youtube Video:
