The Ultimate Guide to Endpoint Intrusion Response: Protect Your Network Today
Endpoint intrusion response is a critical cybersecurity measure that involves detecting and responding to malicious activity targeting endpoints, such as laptops, desktops, and mobile devices. It encompasses a range of techniques, including threat detection, containment, remediation, and recovery, aimed at preventing data breaches, system damage, and business disruptions. By proactively monitoring and responding to endpoint threats, organizations can strengthen their security posture and minimize the impact of cyberattacks.
Endpoint intrusion response systems leverage advanced Technologien, such as machine learning and behavioral analysis, to identify suspicious activities and distinguish between legitimate actions and malicious attempts. When a threat is detected, the system can automatically trigger containment measures to isolate the affected endpoint, preventing the spread of malware or data exfiltration. Additionally, response teams can remotely access the compromised endpoint to perform remediation actions, such as removing malicious software, restoring damaged files, and patching vulnerabilities.
Endpoint intrusion response plays a crucial role in protecting organizations against the evolving threat landscape. By implementing robust endpoint security solutions and adhering to best practices, businesses can significantly reduce their exposure to cyber risks, enhance their resilience, and maintain the integrity of their sensitive data and systems.
Endpoint intrusion response
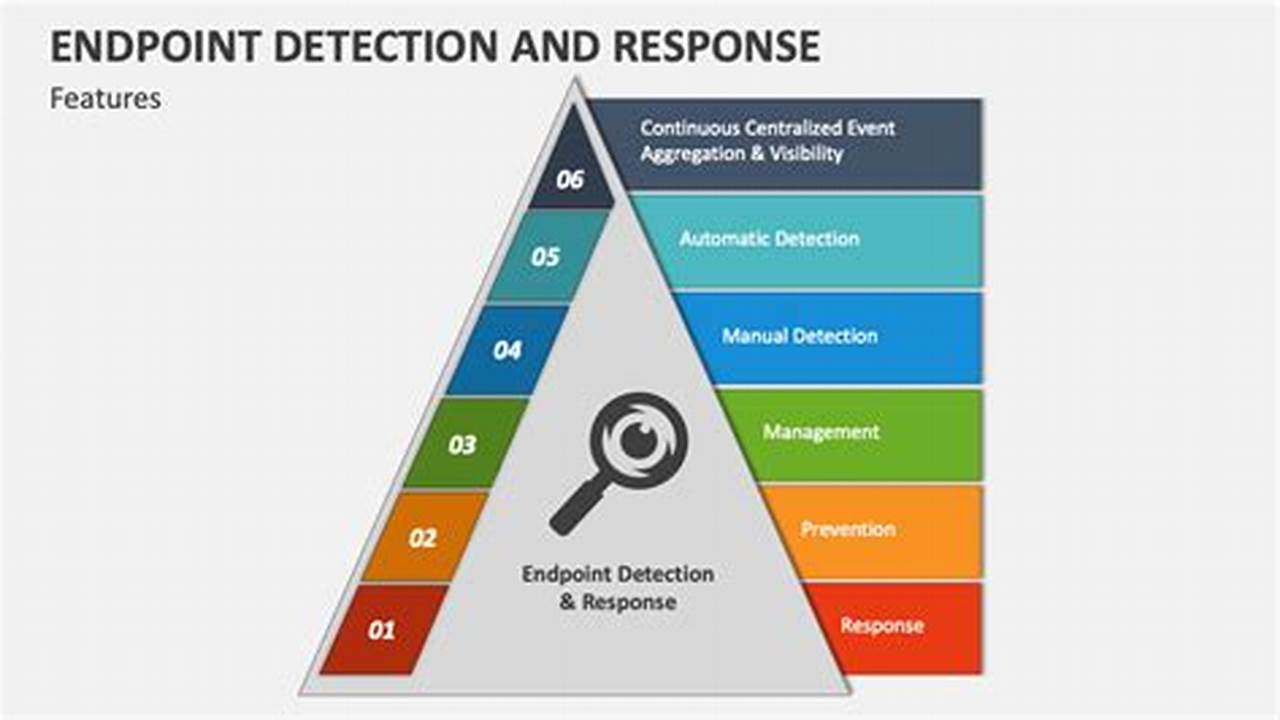
Endpoint intrusion response plays a vital role in safeguarding organizations against cyber threats. It encompasses a comprehensive set of key aspects that work together to detect, contain, and remediate malicious activity targeting endpoints:
- Detection: Identifying suspicious activities and distinguishing between legitimate actions and malicious attempts.
- Containment: Isolating affected endpoints to prevent the spread of malware or data exfiltration.
- Remediation: Removing malicious software, restoring damaged files, and patching vulnerabilities.
- Recovery: Restoring compromised systems to a secure state and minimizing business disruptions.
- Prevention: Implementing proactive measures to strengthen endpoint security and reduce the risk of attacks.
- Response: Establishing incident response plans and procedures to effectively manage and contain threats.
- Monitoring: Continuously monitoring endpoints for suspicious activities and vulnerabilities.
These aspects are interconnected and interdependent, forming a comprehensive approach to endpoint intrusion response. By effectively addressing each of these aspects, organizations can significantly enhance their cybersecurity posture and protect their sensitive data and systems.
Detection
Detection is a critical component of endpoint intrusion response, as it provides the foundation for identifying and responding to malicious activity targeting endpoints. Effective detection capabilities enable organizations to proactively monitor endpoints for suspicious activities and distinguish between legitimate actions and malicious attempts. This distinction is crucial for preventing false positives and ensuring that only genuine threats are addressed.
Endpoint intrusion response systems leverage advanced technologies, such as machine learning and behavioral analysis, to detect suspicious activities. These systems analyze endpoint data, including file access patterns, network connections, and user behavior, to identify anomalies that may indicate malicious activity. For instance, a sudden spike in network traffic or attempts to access sensitive files from an unauthorized location could trigger an alert, prompting further investigation and response.
Accurate and timely detection is essential for effective endpoint intrusion response. By promptly identifying malicious activity, organizations can minimize the potential impact of cyberattacks and take swift action to contain and remediate threats. Conversely, delayed or inaccurate detection can lead to data breaches, system damage, and business disruptions.
Containment
Containment is a critical aspect of endpoint intrusion response, as it enables organizations to limit the impact of malicious activity and prevent the spread of threats across the network. Once a threat has been detected, containment measures are implemented to isolate affected endpoints, effectively preventing the spread of malware or data exfiltration.
- Network Isolation: Affected endpoints can be isolated from the network, preventing further communication with external systems and potential command-and-control servers. This containment measure effectively halts the spread of malware and prevents data exfiltration attempts.
- Process Isolation: Suspicious processes running on affected endpoints can be isolated and terminated, preventing them from executing malicious code or accessing sensitive data. This measure is particularly effective in containing malware that attempts to spread laterally within the network.
- File Access Restriction: Access to specific files or directories on affected endpoints can be restricted, preventing malware from modifying or exfiltrating sensitive data. This containment measure is critical for protecting data integrity and preventing data breaches.
- Endpoint Lockdown: In severe cases, entire endpoints can be locked down, preventing all network access and user interaction. This comprehensive containment measure is used to prevent the spread of highly contagious malware or to preserve evidence for forensic analysis.
Containment measures play a vital role in endpoint intrusion response by preventing the spread of threats and minimizing the potential impact of cyberattacks. By isolating affected endpoints and restricting their activities, organizations can effectively contain malicious activity and buy time to investigate and remediate threats.
Remediation
Remediation is a critical aspect of endpoint intrusion response, as it involves taking decisive actions to remove malicious software, restore damaged files, and patch vulnerabilities to restore the affected endpoint to a secure state.
- Malware Removal: Once malicious software has been detected and contained, it must be removed from the affected endpoint to prevent further damage. This can be achieved using specialized anti-malware tools or by manually identifying and deleting malicious files and processes.
- File Restoration: Malicious activity can often lead to data loss or corruption. Remediation involves restoring damaged or lost files to their original state. This can be achieved using backups or by utilizing data recovery tools.
- Vulnerability Patching: Vulnerabilities in software or operating systems can provide an entry point for malicious actors. Remediation involves patching these vulnerabilities to prevent future attacks. This can be achieved by installing software updates or applying security patches.
Effective remediation measures are essential for endpoint intrusion response, as they enable organizations to restore compromised endpoints to a secure state and prevent the recurrence of malicious activity. By removing malicious software, restoring damaged files, and patching vulnerabilities, organizations can minimize the impact of cyberattacks and maintain the integrity of their systems.
Recovery
Recovery is a crucial component of endpoint intrusion response, as it involves restoring compromised systems to a secure state and minimizing business disruptions. Endpoint intrusion response encompasses the processes and technologies used to detect, contain, and remediate malicious activity targeting endpoints, such as laptops, desktops, and mobile devices. Recovery plays a vital role in ensuring that affected systems are restored to full functionality, data is recovered, and business operations are resumed with minimal disruption.
Effective recovery measures are essential for organizations to maintain business continuity and minimize the impact of cyberattacks. A well-defined recovery plan outlines the steps to be taken to restore compromised systems, including identifying the affected systems, assessing the damage, and implementing appropriate recovery procedures. This plan should also include measures to prevent data loss and ensure the integrity of critical business data. Recovery measures may involve restoring data from backups, rebuilding systems from scratch, or utilizing specialized recovery tools.
By implementing robust recovery measures as part of their endpoint intrusion response strategy, organizations can minimize the downtime and data loss associated with cyberattacks. This proactive approach not only enhances the organization’s security posture but also ensures that business operations can be resumed as quickly as possible, reducing the overall impact of security incidents.
Prevention
Prevention plays a critical role in endpoint intrusion response by implementing proactive measures to strengthen endpoint security and reduce the risk of attacks. By taking a proactive approach, organizations can minimize the likelihood of successful cyberattacks and enhance their overall security posture.
- Endpoint Protection Software: Deploying robust endpoint protection software, including antivirus, anti-malware, and firewall solutions, is essential for preventing malicious software from infiltrating endpoints. These tools continuously monitor endpoints for suspicious activities and threats, providing real-time protection against known and emerging threats.
- Vulnerability Management: Regularly identifying and patching vulnerabilities in operating systems, software, and applications is crucial for preventing attackers from exploiting weaknesses in endpoint security. Organizations should implement a comprehensive vulnerability management program to identify and prioritize vulnerabilities and apply necessary patches promptly.
- User Education and Training: Educating users on cybersecurity best practices and training them to recognize and avoid phishing scams, malicious emails, and other social engineering attacks is essential for preventing endpoint compromise. Empowering users with knowledge and skills can significantly reduce the risk of successful cyberattacks.
- Network Segmentation: Segmenting networks into smaller, isolated zones can limit the spread of malware and prevent attackers from moving laterally across the network. By isolating critical systems and data from less critical areas, organizations can minimize the potential impact of endpoint breaches.
These preventive measures are fundamental in strengthening endpoint security and reducing the risk of attacks. By implementing a comprehensive prevention strategy, organizations can significantly enhance their endpoint intrusion response capabilities and improve their overall cybersecurity posture.
Response
Response plays a critical role within endpoint intrusion response, as it involves establishing comprehensive incident response plans and procedures to effectively manage and contain threats. These plans outline the steps to be taken in the event of an endpoint intrusion, ensuring a coordinated and timely response to minimize the impact and contain the threat.
Incident response plans define the roles and responsibilities of individuals and teams involved in responding to endpoint intrusions, ensuring clear communication and collaboration. They establish protocols for threat identification, containment, eradication, and recovery, providing a structured approach to incident handling. Well-defined response procedures enable organizations to swiftly isolate affected endpoints, prevent the spread of malware, and minimize business disruptions.
For instance, in the aftermath of a ransomware attack targeting endpoints, an organization with a robust incident response plan can quickly activate its response team, isolate infected endpoints, and initiate containment measures to prevent the encryption of additional systems. By having a clear plan in place, the organization can minimize the impact of the attack, recover encrypted data, and restore normal operations with minimal disruption.
Establishing effective incident response plans and procedures is crucial for organizations to respond swiftly and effectively to endpoint intrusions. By outlining clear roles, responsibilities, and procedures, organizations can enhance their ability to contain threats, minimize damage, and maintain business continuity in the face of cyberattacks.
Monitoring
Within the context of endpoint intrusion response, monitoring plays a critical role in proactively identifying and addressing potential threats targeting endpoints. By continuously monitoring endpoints for suspicious activities and vulnerabilities, organizations can gain valuable insights into the security posture of their endpoints and take timely actions to mitigate risks.
- Real-time Threat Detection: Continuous monitoring enables organizations to detect suspicious activities and identify potential threats in real-time. Advanced monitoring tools leverage machine learning algorithms and behavioral analysis techniques to analyze endpoint data, including network traffic, file access patterns, and user behavior, to identify anomalies that may indicate malicious activity.
- Vulnerability Assessment: Monitoring also involves regularly assessing endpoints for vulnerabilities in operating systems, software, and applications. By identifying and prioritizing vulnerabilities, organizations can proactively patch and update their systems, reducing the risk of successful exploitation by attackers.
- Compliance Monitoring: Monitoring can assist organizations in demonstrating compliance with regulatory requirements and industry standards. By maintaining continuous visibility into endpoint activity, organizations can provide evidence of compliance with regulations such as PCI DSS and HIPAA, which mandate the monitoring of endpoints to ensure the protection of sensitive data.
- Proactive Threat Hunting: Continuous monitoring enables organizations to proactively hunt for threats that may evade traditional security mechanisms. By analyzing endpoint data and identifying patterns that deviate from normal behavior, organizations can uncover hidden threats and take proactive measures to mitigate risks.
Effective monitoring practices are essential for organizations to maintain a strong security posture and respond swiftly to endpoint intrusions. By continuously monitoring endpoints for suspicious activities and vulnerabilities, organizations can gain valuable insights into potential threats, prioritize remediation efforts, and minimize the impact of cyberattacks.
Endpoint Intrusion Response
This FAQ section addresses common concerns and misconceptions related to endpoint intrusion response, providing concise and informative answers.
Question 1: What is endpoint intrusion response?
Endpoint intrusion response encompasses the detection, containment, remediation, and recovery processes involved in responding to malicious activity targeting endpoints, such as laptops, desktops, and mobile devices. It aims to minimize the impact of cyberattacks by swiftly identifying and addressing threats.
Question 2: Why is endpoint intrusion response important?
Endpoint intrusion response is crucial for organizations to protect their sensitive data, maintain business continuity, and comply with regulatory requirements. By effectively responding to endpoint threats, organizations can prevent data breaches, system damage, and financial losses.
Question 3: What are the key components of endpoint intrusion response?
Endpoint intrusion response involves several key components, including threat detection, containment, remediation, recovery, prevention, response, and monitoring. Each component plays a vital role in protecting endpoints from malicious activity.
Question 4: How can organizations improve their endpoint intrusion response capabilities?
Organizations can enhance their endpoint intrusion response capabilities by implementing robust endpoint protection software, regularly patching vulnerabilities, educating users on cybersecurity best practices, segmenting networks, and establishing clear incident response plans.
Question 5: What are the benefits of continuous monitoring for endpoint intrusion response?
Continuous monitoring enables organizations to proactively identify suspicious activities and vulnerabilities, assess compliance, and hunt for hidden threats. It provides valuable insights into the security posture of endpoints, allowing organizations to respond swiftly to potential threats.
Question 6: How can organizations ensure effective endpoint intrusion response?
To ensure effective endpoint intrusion response, organizations should establish clear roles and responsibilities, conduct regular training and exercises, use automated tools to streamline response processes, and continuously evaluate and improve their endpoint security measures.
In summary, endpoint intrusion response is a critical aspect of cybersecurity, enabling organizations to safeguard their endpoints from malicious activity and minimize the impact of cyberattacks. By understanding the key components, benefits, and best practices associated with endpoint intrusion response, organizations can enhance their security posture and protect their valuable assets.
Transition to the next article section: Endpoint intrusion response plays a vital role in protecting organizations from cyber threats. Let’s delve deeper into the specific techniques and technologies used for endpoint intrusion detection and response.
Endpoint Intrusion Response Best Practices
Effective endpoint intrusion response requires a comprehensive approach that encompasses proactive measures, timely detection, and efficient remediation. Here are several best practices to enhance your endpoint intrusion response capabilities:
Implement a layered security approach: Deploy multiple layers of security controls, including endpoint protection software, network firewalls, and intrusion detection/prevention systems, to create a robust defense against endpoint threats.
Enforce regular software updates: Regularly patch operating systems, applications, and firmware to address vulnerabilities and reduce the risk of successful exploitation by attackers.
Educate users on cybersecurity best practices: Train users to recognize and avoid phishing emails, malicious websites, and social engineering attacks to minimize the risk of endpoint compromise.
Implement network segmentation: Divide your network into smaller, isolated zones to limit the spread of malware and prevent attackers from moving laterally across the network.
Establish a clear incident response plan: Define roles, responsibilities, and procedures for responding to endpoint intrusions to ensure a coordinated and effective response.
Utilize threat intelligence: Monitor threat intelligence feeds and share information with other organizations to stay informed about emerging threats and potential vulnerabilities.
Conduct regular security audits: Regularly assess your endpoint security measures to identify weaknesses and make necessary improvements to your intrusion response strategy.
By adhering to these best practices, organizations can significantly strengthen their endpoint intrusion response capabilities, minimize the impact of cyberattacks, and protect their sensitive data and systems.
In conclusion, endpoint intrusion response is a critical aspect of cybersecurity. By adopting a proactive and comprehensive approach that incorporates these best practices, organizations can enhance their ability to detect, contain, and remediate endpoint threats, ensuring the security and integrity of their IT infrastructure.
Endpoint Intrusion Response
Endpoint intrusion response is a critical component of an organization’s cybersecurity strategy, enabling the timely detection, containment, and remediation of threats targeting endpoints. This comprehensive approach involves implementing robust security measures, educating users, and establishing clear incident response plans.
Effective endpoint intrusion response requires a proactive and collaborative approach, involving collaboration between IT security teams, business units, and end-users. By adhering to best practices, organizations can enhance their ability to safeguard their sensitive data, maintain business continuity, and minimize the impact of cyberattacks.
Youtube Video:
