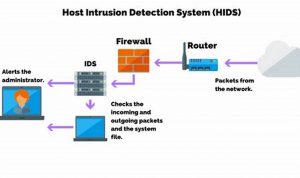
Host detection and response (HDR) is a crucial cybersecurity strategy that enables organizations to identify, contain, and remediate threats to […]
Tag: response
The Ultimate Guide to Cybersecurity Incident Response for Security Experts
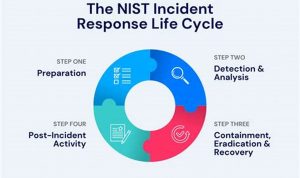
Cybersecurity incident response is the process of responding to and recovering from a cybersecurity incident. It involves identifying the incident, […]
Cyber Security's Guide to Advanced Detection and Response
Advanced detection and response is a security concept that involves using advanced technologies and techniques to detect and respond to […]
All-Encompassing Endpoint Incident Response Strategies
Endpoint incident response is a critical aspect of modern cybersecurity. It refers to the strategies and actions taken to detect, […]
Essential Threat Response Tools for Robust Cybersecurity
Threat response tools empower organizations to proactively manage and mitigate potential risks and incidents. These tools provide real-time monitoring, threat […]
Automate Your Threat Response: Enhanced Security with Cutting-Edge Technology
Threat response automation is the use of technology to automate the detection, investigation, and response to cyber threats. This can […]
Latest Automated Response Innovations in Cybersecurity
Automated response refers to a pre-programmed or predetermined response generated by a computer system or software without human intervention. It […]
The Definitive Guide to Incident Detection and Response in Modern Cybersecurity
Incident detection and response is the process of identifying and responding to security incidents. It involves detecting suspicious activity, investigating […]
Expert Endpoint Security Response for Enhanced Cyber Protection
Endpoint security response is a set of security measures designed to protect endpoints, which are devices such as laptops, desktops, […]
Strategies for Countering Cybersecurity Threats: A Comprehensive Guide
Cybersecurity threat response encompasses the processes and procedures employed to detect, analyze, and mitigate potential threats to an organization’s cybersecurity […]