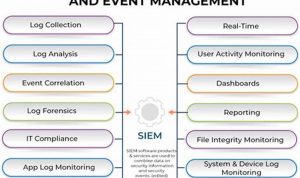
Security information management (SIM) is the process of collecting, analyzing, and reporting on security-related information from multiple sources within an […]
Tag: management
Masterful Security Incident Management: Shielding Your Digital Fortress
Security incident management is the process ofidentifying,responding to, and recovering from security incidents. It is a critical part of anyorganization’s […]
Effective Incident Management: Strategies for Enhancing Security and Mitigating Risks
Incident management is a systematic approach to managing unplanned interruptions to an organization’s services or operations. An incident can be […]
The Ultimate Guide to Vulnerability Management: Protecting Your Systems and Data
Vulnerability management is the continuous process of identifying, assessing, and mitigating vulnerabilities in information systems. It involves identifying weaknesses in […]
Secure Your Endpoints: A Comprehensive Guide to Endpoint Risk Management
Endpoint risk management refers to the strategies and practices employed to identify, assess, mitigate, and monitor risks associated with endpointdevices. […]
Ultimate Guide: Security Risk Management for Enhanced Cyber Security
Security risk management is a crucial aspect of safeguarding sensitive information and critical assets against potential threats and vulnerabilities. It […]
Essential Endpoint Security Management: Protect Your Network from Cyber Threats
Security endpoint management refers to the security measures and technologies used to protect endpoints, which are devices such as laptops, […]
Master Endpoint Security Management for Bulletproof Cyber Defense
Endpoint security management is the practice of protecting endpoints, such as laptops, desktops, and mobile devices, from unauthorized access and […]
The Ultimate Guide to Mastering Security Event Management
Security event management (SEM) is a process that involves collecting, monitoring, and analyzing security events to identify and mitigate potential […]