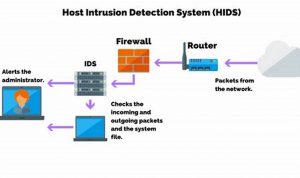
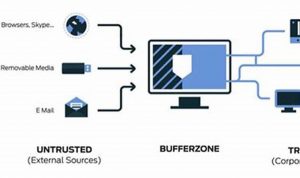
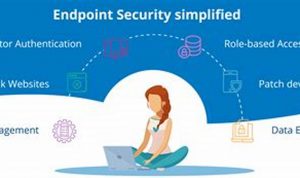
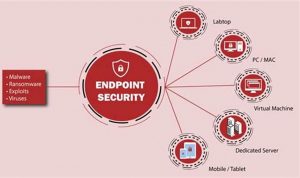
Endpoint threat monitoring is the practice of monitoring endpoints, such as laptops, desktops, and servers, for malicious activity. This can […]
Tag: endpoint
The Ultimate Guide to Endpoint Visibility for Enhanced Cybersecurity
Endpoint visibility refers to the ability to monitor and manage endpoints, which are devices such as laptops, desktops, and smartphones […]
Ultimate Guide to Endpoint Breach Detection for Unstoppable Cybersecurity
Endpoint breach detection is a cybersecurity measure focused on identifying and responding to security breaches that target endpoints, the devices […]
All-Encompassing Endpoint Incident Response Strategies
Endpoint incident response is a critical aspect of modern cybersecurity. It refers to the strategies and actions taken to detect, […]
Essential Endpoint Isolation: Protect Your Network from Threats
Endpoint isolation is a cybersecurity measure that involves isolating endpoints, such as laptops, desktops, and mobile devices, from the rest […]
Comprehensive Endpoint Threat Intelligence: Protect Your Devices
Endpoint threat intelligence gathers and analyzes data to provide comprehensive insights into potential threats and vulnerabilities at endpoints, which are […]
Expert Endpoint Security Response for Enhanced Cyber Protection
Endpoint security response is a set of security measures designed to protect endpoints, which are devices such as laptops, desktops, […]
Secure Your Endpoints: Comprehensive Endpoint Detection Platform for Cyber Threats
An endpoint detection platform (EPP) is a software solution that monitors and analyzes activities on endpoints (such as laptops, desktops, […]
Complete Endpoint Security Guide for Enhanced Cyber Protection
Endpoint security is a critical component of any organization’s cybersecurity strategy. It involves protecting devices such as laptops, desktops, smartphones, […]
Ultimate Protection:Endpoint Attack Prevention for Maximum Security
Endpoint attack prevention, a critical component of cybersecurity, involves safeguarding endpoints such as laptops, desktops, servers, and mobile devices from […]